CYBER SECURITY TRAINING IN NAGPUR
-

-
(11163 Reviews)
-
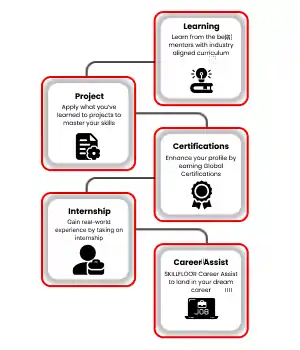
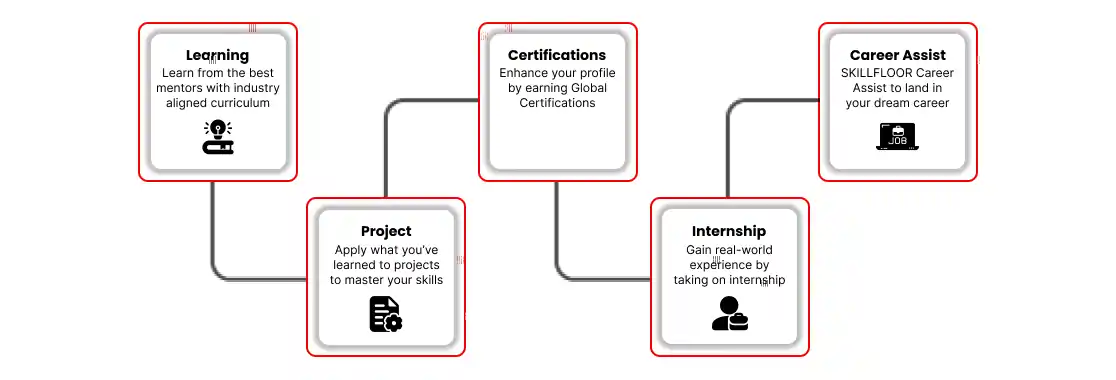
Exciting Career Options: Discover the top job opportunities in Nagpur's cyber security field. Get ready for roles like security analyst or ethical hacker.
-
Key Skills You Need: Learn essential skills like securing networks, analyzing threats, and managing risks to safeguard businesses online.
-
Practical Training: Build real-world experience through internships with top companies. Improve your skills and confidence for a successful career in cyber security.