CYBER SECURITY TRAINING IN DEHRA DUN
-

-
(16480 Reviews)
-
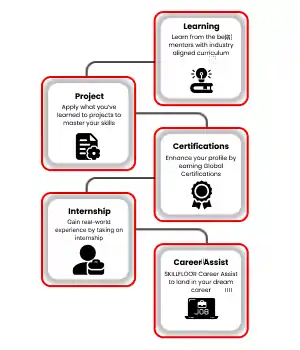
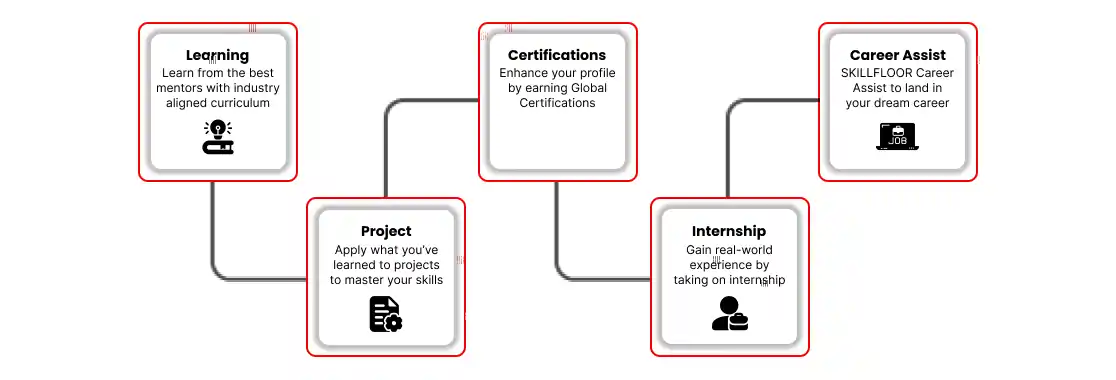
Exciting Career Opportunities: Explore the best job openings in Dehra Dun’s cyber security field. Prepare for top roles like security analyst or ethical hacker, and take the first step toward an exciting career in protecting digital assets.
-
Essential Skills for Success: Master the most important skills such as network security, threat analysis, and risk management to safeguard businesses from online threats and vulnerabilities.
-
Hands-On Training Experience: Gain valuable real-world experience through internships with leading companies in Dehra Dun. Enhance your skills and confidence to thrive in the growing field of cyber security.