CYBER SECURITY TRAINING IN AURANGABAD
-

-
(15344 Reviews)
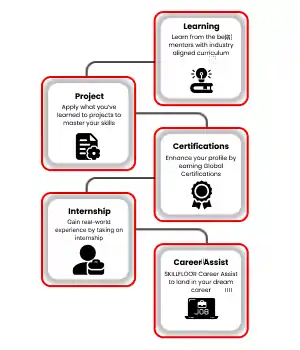
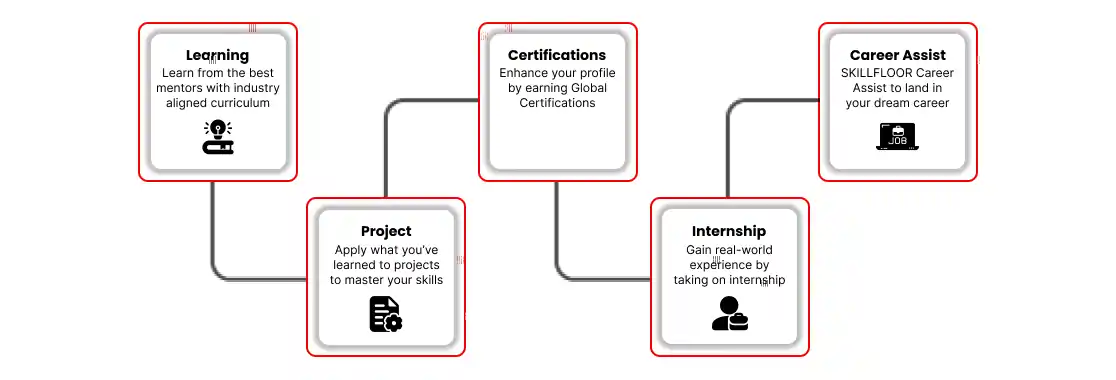
- Skills: Gain key cybersecurity skills such as network security, ethical hacking, incident response, and risk management.
- Career: Explore various career paths, such as cybersecurity analyst, penetration tester, security consultant, or network security engineer.
- Syllabus: Dive into topics like threat detection, cryptography, secure coding, compliance frameworks, and cybersecurity management in this in-depth training program.