CYBER SECURITY TRAINING IN PONDICHERRY
-

-
(16331 Reviews)
-
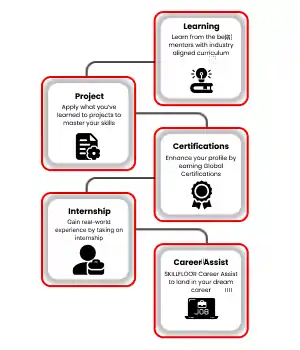
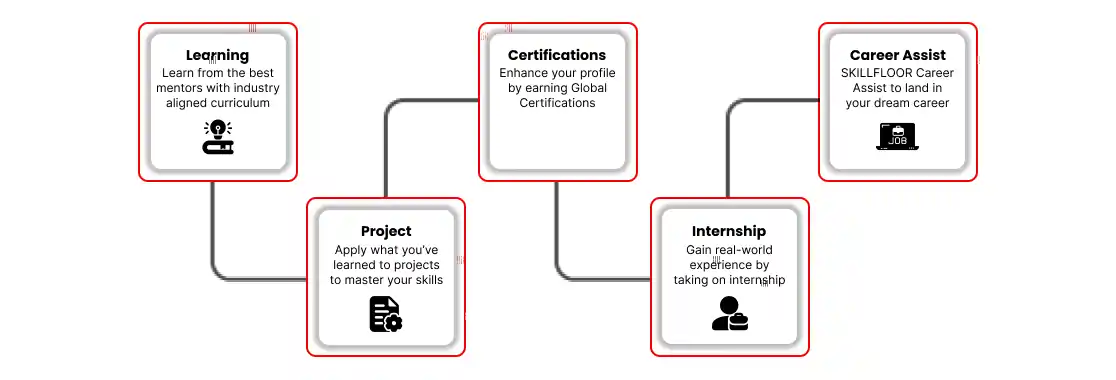
Top Career Options: Discover exciting job opportunities in Pondicherry's cybersecurity industry. Get ready for roles like security analyst or network defender.
-
Key Skills to Learn: Focus on essential skills such as ethical hacking, identifying threats, and protecting data to excel in the digital field.
-
Real-World Experience: Boost your knowledge and confidence with internships at top companies. Build practical skills to kickstart a successful cybersecurity career.