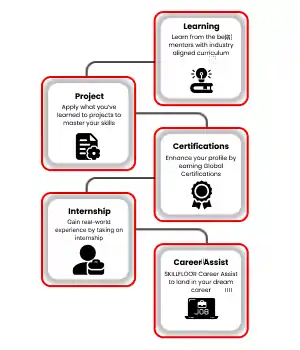
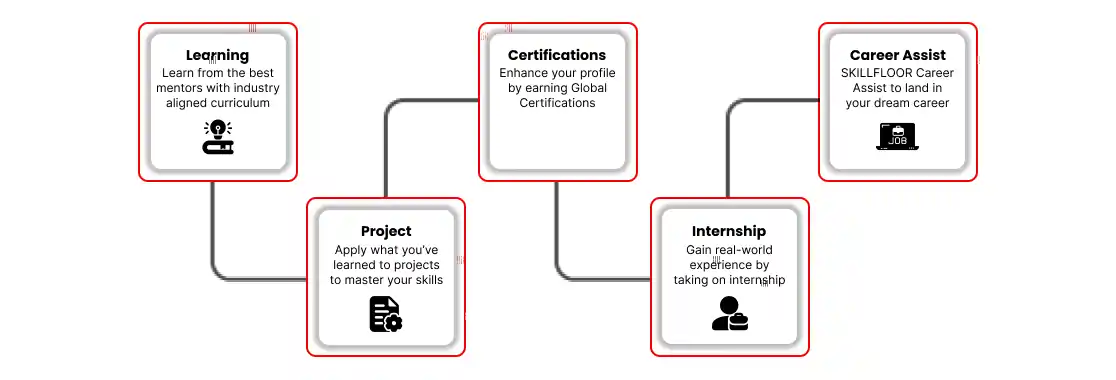
CYBER SECURITY TRAINING IN TIRUCHCHIRAPPALLI
-

-
(10032 Reviews)
-
Skills: Learn important cybersecurity skills such as protecting networks, ethical hacking, handling security incidents, and managing risks.
-
Career: Explore different job roles in cybersecurity, like security analyst, penetration tester, security consultant, or network security engineer.
-
Syllabus: Gain knowledge on detecting threats, encryption, secure coding, industry standards, and managing cybersecurity through this detailed training program, available in Tiruchchirappalli.