Cybersecurity is a rapidly growing field and one of the most in-demand careers in the current job market. With the increasing threat of cyber attacks and malicious activities, organizations and individuals are seeking expert help in protecting their sensitive information and data. New York City, being the financial capital of the world and a major hub for technological innovations, offers ample opportunities for pursuing a career in cybersecurity. cyber security courses in New York City are designed to provide the necessary knowledge and skills to individuals interested in this field. These courses cover a broad range of topics, including threat assessment, security architecture, identifying and managing vulnerabilities, incident response, and compliance regulations. The courses are typically delivered in a blended format, combining online self-paced learning with live instructor-led sessions. This approach allows students to complete the coursework at their own pace while still benefiting from the expertise of knowledgeable instructors. New York City is home to many prestigious universities and colleges that offer cybersecurity courses, including New York University (NYU), Columbia University, and the City University of New York (CUNY). NYU's Tandon School of Engineering has a Cybersecurity Master's Program that offers courses designed to give students a full understanding of the field of cybersecurity. Columbia University offers a Master of Science in Data Science with a focus on Cybersecurity that covers topics such as cryptography, network security, and applied information security. In addition to traditional universities, there are also several specialized cybersecurity training institutes in New York City that provide hands-on training and certification courses. These courses are typically short-term and designed for individuals seeking to enhance their existing cybersecurity skills or transition into the field. SANS Institute's New York City campus offers intensive training courses that cover a wide range of cybersecurity topics, including ethical hacking, penetration testing, and incident handling. The International Association of Computer Investigative Specialists (IACIS) offers a certification program that teaches students to handle digital evidence and conduct investigations. Cybersecurity professionals in New York City can expect to earn competitive salaries, with the average salary for cybersecurity professionals in the city being around $100,000 per year. Entry-level cybersecurity jobs typically start at around $60,000 per year, with experienced professionals earning upwards of $130,000 per year. The demand for cybersecurity professionals is expected to grow in the coming years, with the Bureau of Labor Statistics projecting a growth rate of 31% in the cybersecurity field between 2019 and 2029. In conclusion, pursuing a career in cybersecurity in New York City can be a lucrative and fulfilling path. With a range of cybersecurity courses and training institutes to choose from, individuals seeking to advance their cybersecurity skills or transition into the field have a wealth of opportunities available to them. As the demand for cybersecurity professionals continues to grow, taking cybersecurity courses in New York City can provide a competitive edge in this rapidly growing field.

₹60,000


Hurry Up!
Limited seats call us now for amazing discounts on digital maketing course

Skillfloor is officially recognized by the Government of India as a Startup India (DPIIT) certified institute — a mark of trust in the quality of our courses and career-focused learning.
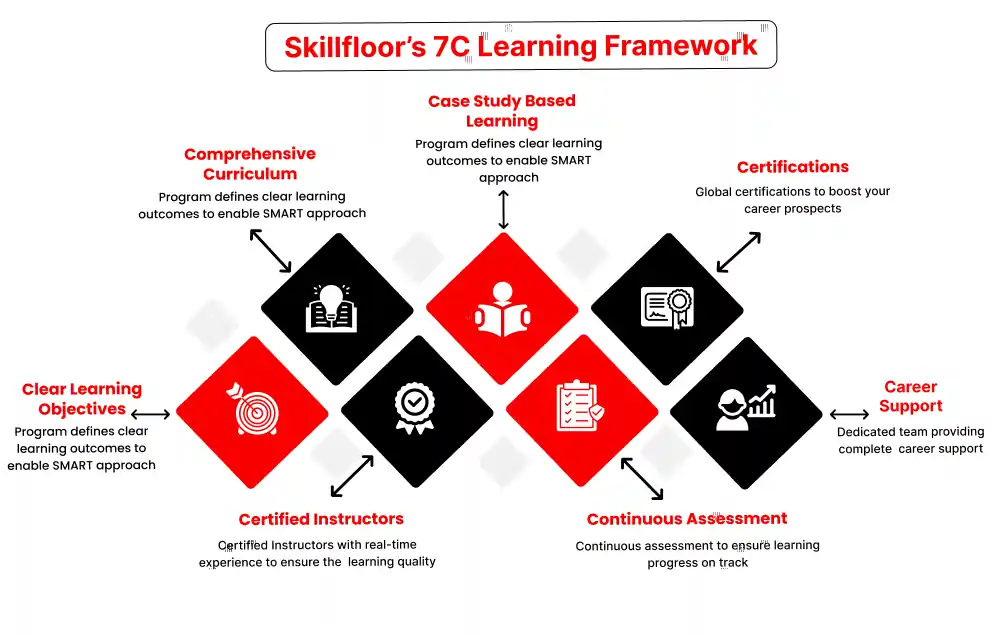
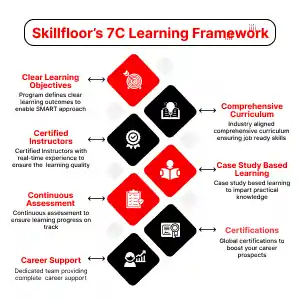
We offer hands-on programs across multiple fields, designed by industry experts to help you gain skills that employers value:
Digital Marketing – Grow businesses online with SEO, social media, and analytics.
AI & Machine Learning – Build practical AI skills for real-world applications.
Ethical Hacking & Cybersecurity – Protect networks and systems from cyber threats.
Data Analytics & Data Science – Analyze data and make smarter decisions.
Other Emerging Technologies – Learn trending, in-demand skills.
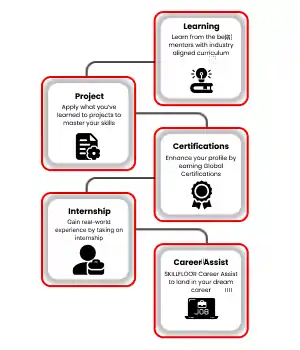
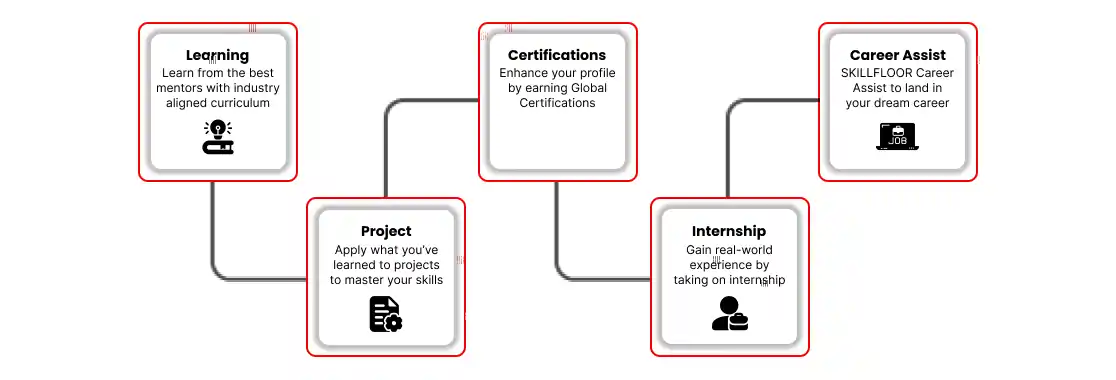
At Skillfloor, you don’t just learn — you practice, complete live projects, and prepare for real career opportunities. Whether you’re a student, graduate, or working professional, we help you upgrade your skills and grow confidently in your career.
Join a government-recognized institute shaping India’s next generation of skilled professionals.



- Overview of Cyber Security Concepts
- Types of Cyber Threats (Malware, Ransomware, Phishing, etc.)
- Cybersecurity Frameworks and Standards (NIST, ISO 27001)
- The Role of Cyber Security in Organizations
- Key Cyber Security Terminology (Vulnerabilities, Risks, Threats)
- Understanding Networking Basics (IP, DNS, TCP/IP)
- Network Security Devices: Firewalls, Routers, and Switches
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
- Secure Network Design and Segmentation
- Virtual Private Networks (VPNs) and Secure Communication Protocols
- Confidentiality, Integrity, and Availability (CIA Triad)
- Risk Management Processes (Assessment, Mitigation, Response)
- Types of Security Controls (Preventive, Detective, Corrective)
- Security Policies and Standards (ISO, NIST)
- Security Audits and Compliance Requirements (SOX, GDPR)
- Basics of Cryptography: Symmetric vs Asymmetric Encryption
- Public Key Infrastructure (PKI) and Digital Certificates
- Common Cryptographic Algorithms (AES, RSA, ECC)
- Digital Signatures and Certificates
- Hashing Algorithms and Their Applications (SHA, MD5)
- Common Web Application Vulnerabilities (SQL Injection, XSS)
- OWASP Top 10: Key Vulnerabilities and Mitigation
- Secure Software Development Lifecycle (SSDLC)
- Web Application Firewalls (WAF) and Their Role
- Authentication and Session Management Best Practices
- Phases of Penetration Testing: Reconnaissance, Scanning, Exploitation
- Vulnerability Scanning and Risk Assessment
- Tools for Ethical Hacking: Nmap, Metasploit, Burp Suite
- Social Engineering Attacks and Mitigation
- Writing Penetration Testing Reports and Documentation
- Incident Response Lifecycle: Identification, Containment, Eradication
- Incident Response Plans and Team Structure
- Forensic Analysis of Cyber Incidents
- Collecting and Preserving Digital Evidence
- Using SIEM (Security Information and Event Management) for Monitoring
- Understanding Cloud Computing Models (IaaS, PaaS, SaaS)
- Security Challenges in the Cloud: Data Breaches, Misconfigurations
- Shared Responsibility Model in Cloud Security
- Cloud Security Best Practices (Encryption, Access Control)
- Securing Cloud Platforms: AWS, Microsoft Azure, Google Cloud
- Authentication Mechanisms: Passwords, Biometric, 2FA, MFA
- Role-Based Access Control (RBAC) vs. Attribute-Based Access Control (ABAC)
- Single Sign-On (SSO) and Federation
- Privileged Access Management (PAM)
- Identity and Access Management Solutions (Okta, Azure AD)
- Overview of Data Protection Laws (GDPR, HIPAA, PCI-DSS)
- Cybersecurity Compliance Frameworks (NIST, CIS Controls)
- Data Privacy Regulations and Their Implications
- Legal Requirements for Incident Reporting and Data Breach Notifications
- Understanding Cyber Liability Insurance and Legal Risks