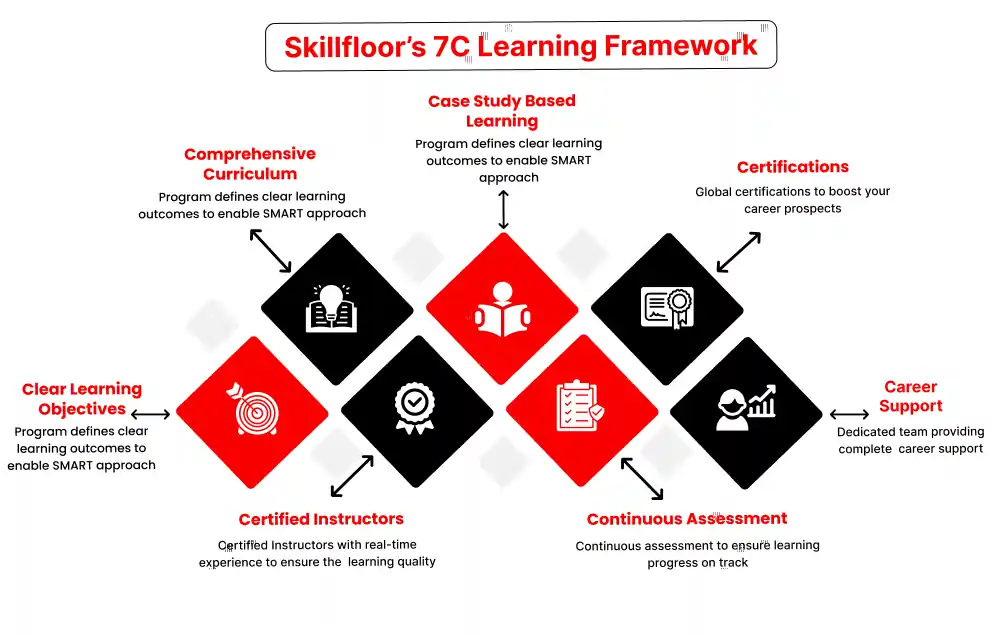
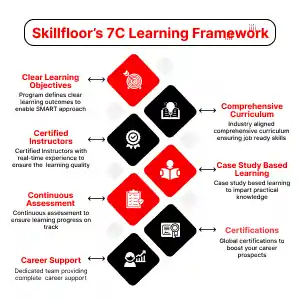
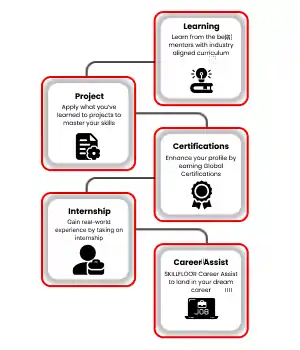
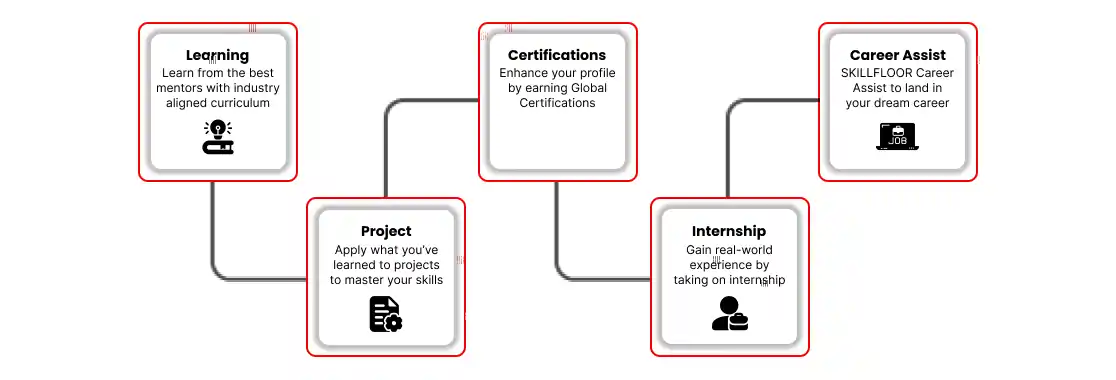
Certified Penetration Testing Professional
SF-CS-CPTP-1115
-

-
(238 Reviews)
- Career: Gain career mobility by earning the Certified Penetration Testing Associate qualification, which can lead to positions in penetration testing, ethical hacking, and cybersecurity consulting.
- Skills: To effectively address security concerns, gain critical skills in network scanning, finding vulnerabilities, exploit building, and report writing.
- Internship: To gain practical experience in penetration testing under the direction of professionals, look for internships with top cybersecurity companies.