Ethical Hacking
-

-
(2664 Reviews)
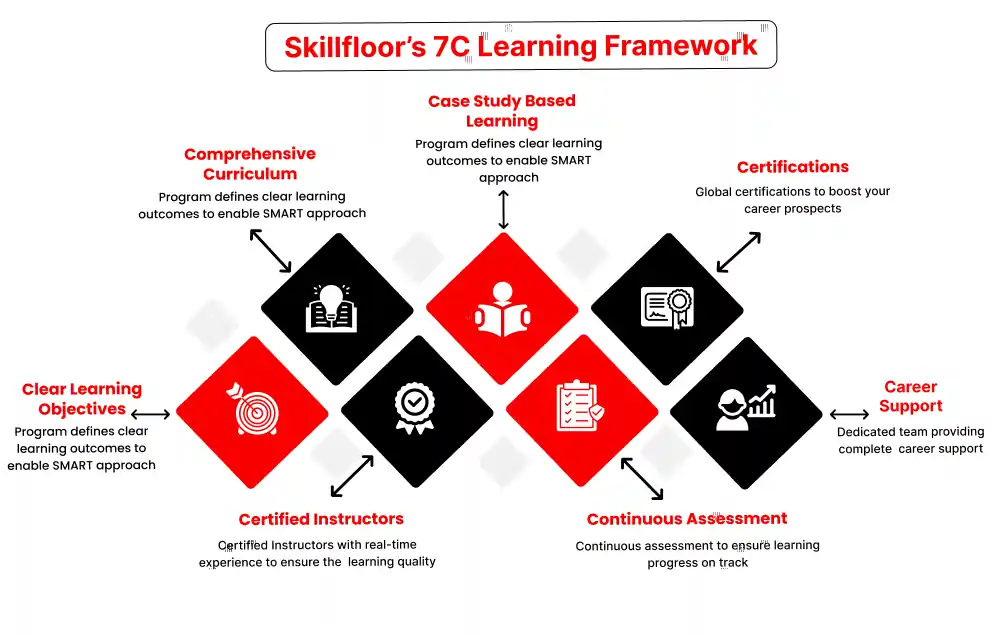
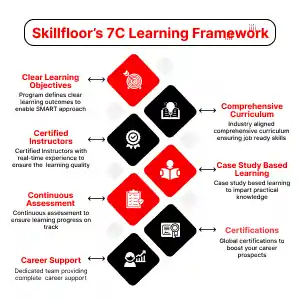
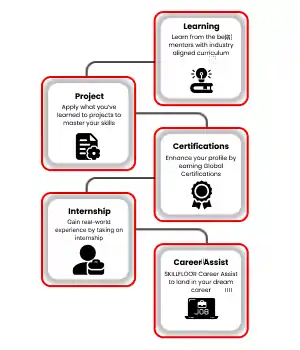
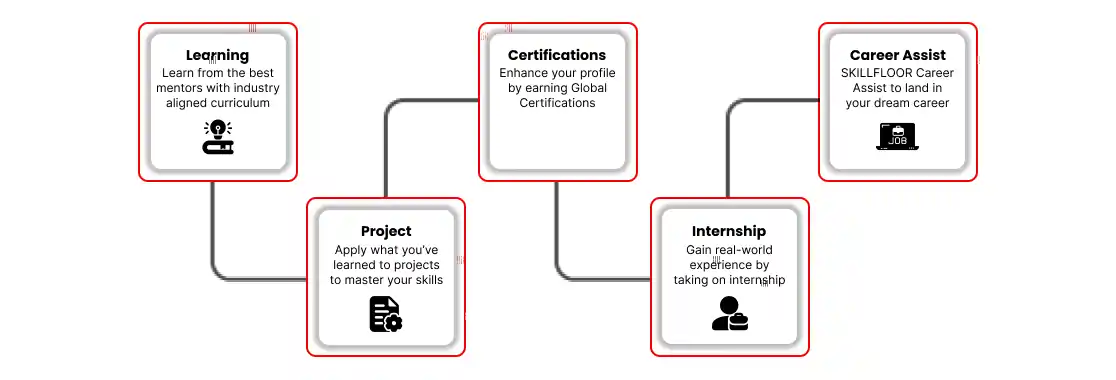
- Career: Advance your cybersecurity job by taking the lead in plans, management, and control while supporting creativity and agility in cybersecurity procedures.
- Skills: By constantly expanding your skills in fields like threat analysis, digital forensics, risk management, and security architecture
- Flexible Learning: To fit your schedule and learning preferences, select from a range of learning methods, such as online courses, workshops, and hands-on labs.