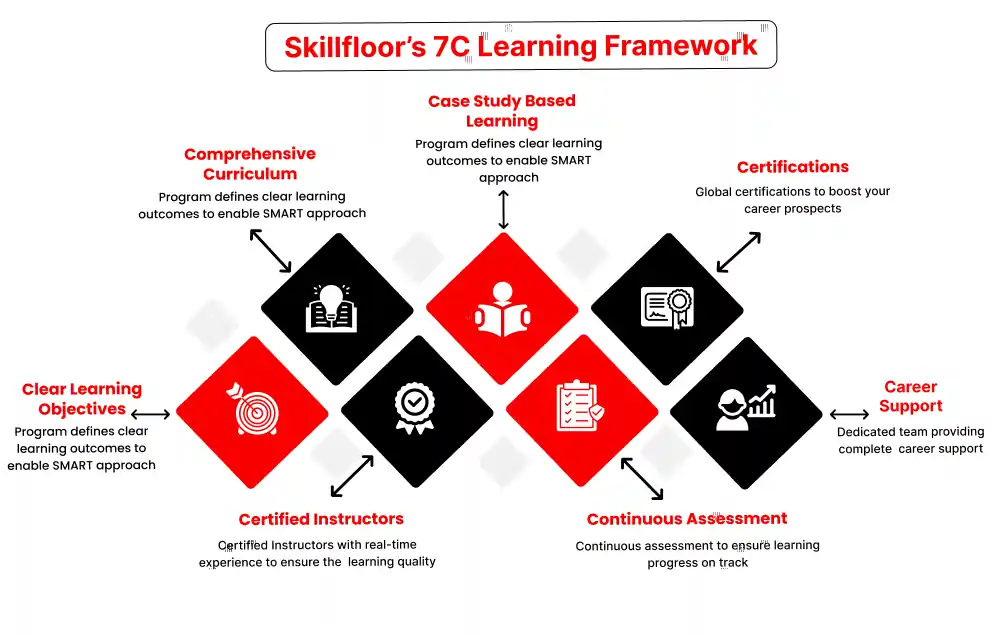
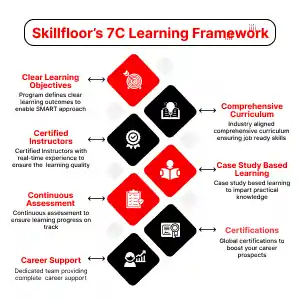
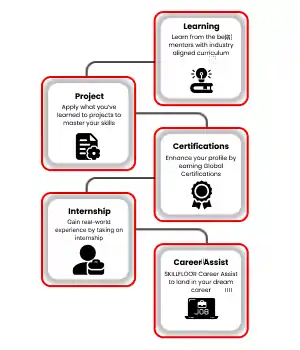
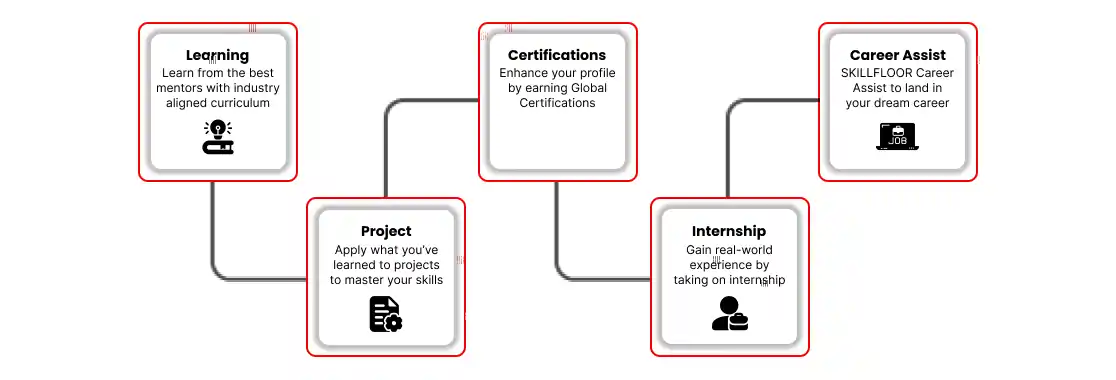
Certified Ethical Hacking Professional
SF-CS-CEHP-1117
-

-
(354 Reviews)
- Career: Open doors to fulfilling careers in the quickly growing cloud security industry, such as those of a cloud security analyst, cloud security engineer, or cloud security consultant.
- Skills: Keeping your skill set will help you stay up to date on the latest developments in cloud security trends and technologies.
- Internship: Increase your chances of securing a full-time 1-Month internship through valuable experience and references.