What is Ethical Hacking?
Learn about ethical hacking, its importance in cybersecurity, how it differs from malicious hacking, key tools, certifications, and its role in protecting data.

Nowadays, where almost everything is connected online, security is more important than ever. Every day, businesses and individuals face threats from hackers who break into systems and steal sensitive information. These cyber-attacks can cause big financial losses, hurt reputations, and put people's privacy at risk. However, there is a group of people who work to prevent these attacks before they happen — ethical hackers.
You might be wondering, “What’s the difference between an ethical hacker and a regular hacker?”
Understanding the Value of Ethical Hacking
The problem we face today is that cyber-attacks are becoming more common, and they are often more sophisticated. Hackers are using advanced tools and strategies to break into systems and steal information. This is a big issue for businesses and individuals who store private data online. At the same time, many organizations don’t realize how important it is to check their security before they face a real attack.
That’s where ethical hackers come in. They find weaknesses in systems, but they do it with permission and for a good cause — to prevent the bad hackers from harming. However, because many people don’t fully understand ethical hacking, it can be hard to see how valuable it is.
What is ethical hacking, how does it differ from illegal hacking, and why is it important?
What is Ethical Hacking?
At its core, ethical hacking refers to the practice of deliberately probing systems and networks for weaknesses, with the permission of the organization, to improve security. Unlike malicious hackers, ethical hackers (also known as "white-hat hackers") act with authorization and work to identify potential weaknesses before criminals can exploit them. Their mission is simple: to prevent cyber threats by finding flaws and fixing them.
Ethical hackers use the same tools and techniques as black-hat hackers (the illegal ones), but their goal is to make systems stronger, not to compromise them. Think of them as digital detectives who search for hidden weaknesses in the virtual world and work with the affected organization to address these problems.
Why is Ethical Hacking Important?
As I’ve mentioned, cybersecurity is more important than ever. Organizations today face advanced threats, ranging from ransomware and phishing to advanced persistent threats (APTs) and insider attacks. Cybercriminals are increasingly using automated tools to launch large-scale attacks, often targeting multiple systems at once. These attacks can result in financial losses, reputational damage, and legal consequences without proper defense mechanisms.
This is where ethical hacking becomes indispensable. Ethical hackers conduct penetration testing, vulnerability assessments, and security audits to evaluate a system's security posture. By doing so, they help organizations uncover and address weaknesses before they can be exploited.
Think of it this way: If you wanted to lock your doors at night but didn’t have a key, wouldn’t you first test whether the locks were functional? Ethical hackers do exactly that. They simulate attacks to identify what could go wrong, helping businesses tighten their defenses and ultimately avoid costly security breaches.
The Difference Between Ethical Hacking and Malicious Hacking
One of the most important aspects of ethical hacking is understanding how it differs from malicious hacking. While both ethical hackers and malicious hackers have the skills to exploit system vulnerabilities, their intentions are entirely different.
-
Malicious Hacking (Black-hat Hacking): This is an illegal form of hacking. Black-hat hackers infiltrate systems with harmful intent — stealing personal data, defacing websites, or crippling organizations for financial gain. Their actions are unauthorized and often criminal.
-
Ethical Hacking (White-hat Hacking): Ethical hackers, on the other hand, work with permission and under a legal framework. They use their skills to assess the security of systems and help organizations shore up vulnerabilities. Ethical hacking is a legitimate practice, carried out by security professionals to enhance safety and protect data.
This fundamental difference in intent is what sets ethical hackers apart. They are trusted partners to organizations, while black-hat hackers are criminals. Ethical hackers are also bound by legal and ethical guidelines to ensure that their actions do not cause harm.
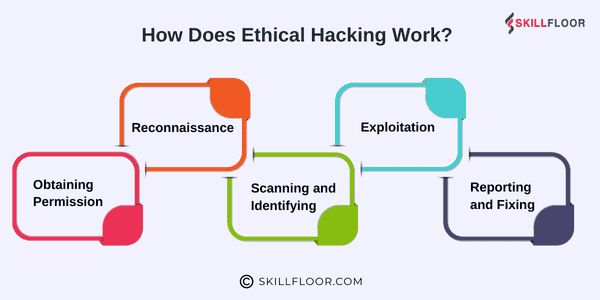
How Does Ethical Hacking Work?
Ethical hacking involves several steps, all aimed at identifying vulnerabilities and strengthening defenses. Here’s a breakdown of how ethical hackers typically approach a project:
-
Obtaining Permission: Before ethical hackers begin testing, they must obtain explicit authorization from the organization to access their systems. This step ensures that the testing is legal and protects both parties.
-
Reconnaissance: Once authorized, ethical hackers perform reconnaissance, gathering information about the target system. This might include publicly available data or specific system information. The goal is to understand the target in detail, identifying potential entry points.
-
Scanning and Identifying Vulnerabilities: Ethical hackers use a variety of scanning tools to test for vulnerabilities. They may look for outdated software, weak passwords, misconfigurations, and other flaws that could be exploited by cybercriminals.
-
Exploitation: After identifying vulnerabilities, ethical hackers attempt to exploit them in a controlled environment to see if they can gain access to the system. This step is crucial for understanding the severity of the risks.
-
Reporting and Fixing: Once the testing is complete, ethical hackers provide a detailed report to the organization. This includes an analysis of vulnerabilities found, how they were exploited, and recommendations for addressing them. The organization then takes the necessary steps to patch these vulnerabilities and strengthen its defenses.
The Tools of Ethical Hackers
Ethical hackers rely on a variety of tools to conduct their tests. These tools help them scan, analyze, and exploit system vulnerabilities. Some of the most commonly used tools in ethical hacking include:
-
Wireshark: A network protocol analyzer used to capture and analyze data packets. It’s often used to detect malicious activity on a network.
-
Metasploit: A penetration testing tool that helps ethical hackers identify and exploit vulnerabilities in systems.
-
Burp Suite: A popular suite of tools for web application security testing, used to find vulnerabilities like SQL injection and cross-site scripting (XSS).
-
Nmap: A network scanning tool used to discover devices and services running on a network and identify potential security flaws.
These tools help ethical hackers gather information, scan networks, and exploit vulnerabilities — all in a controlled, ethical manner.
Ethical Hacking Certifications and Skills
Ethical hacking is a specialized field that requires a solid understanding of cybersecurity concepts and technical skills. To pursue a career in ethical hacking, individuals typically need to obtain certifications, gain experience, and develop a range of skills.
Certifications
Some of the most recognized certifications for ethical hackers include:
-
Certified Ethical Hacker (CEH): One of the most well-known certifications, CEH provides in-depth knowledge of ethical hacking techniques and tools.
-
Offensive Security Certified Professional (OSCP): OSCP is a hands-on certification that tests a candidate's ability to exploit vulnerabilities in real-world environments.
-
Certified Information Systems Security Professional (CISSP): While not exclusively focused on ethical hacking, CISSP is a comprehensive certification for those pursuing a career in information security.
Skills
In addition to certifications, ethical hackers need a combination of technical and soft skills, including:
-
Programming: Knowledge of programming languages like Python, C, or JavaScript is essential for identifying flaws in code and writing exploits.
-
Networking: A deep understanding of networking protocols (TCP/IP, DNS, HTTP, etc.) is crucial for assessing vulnerabilities in network systems.
-
Problem-Solving: Ethical hackers need to think critically and creatively to find ways into systems and identify weak spots.
-
Communication: After completing their assessments, ethical hackers must be able to clearly communicate their findings to stakeholders and suggest improvements.

Why Ethical Hacking is Important and How SKILLFLOOR Helps
Cybersecurity is more important than ever because cyberattacks are on the rise. Ethical hackers help protect systems by finding and fixing security problems before bad hackers can take advantage of them. As the need for skilled cybersecurity professionals grows, ethical hacking is becoming a great career choice.
At SKILLFLOOR, we help students learn practical skills that will help them succeed in their careers. Since 2013, we’ve been offering hands-on courses that teach real-world skills. Through our partnerships with DataMites and Skillogic, we offer top courses like the Certified Ethical Hacker (C|EH) certification, the Certified Penetration Testing Professional (CPPT), and the Certified Ethical Hacking Professional (CEHP), all designed to prepare students for successful careers in ethical hacking and cybersecurity.
Legal and Ethical Considerations in Ethical Hacking
As an ethical hacker, you must always act within the boundaries of the law. Unauthorized hacking — even if it’s for a good cause — is illegal and can lead to serious consequences. Ethical hackers are required to operate under a contract or agreement with the organization, which specifies the scope of their work and the actions they are authorized to take.
Ethical hackers must also adhere to ethical guidelines. They should not misuse any data they access during testing, and they should always ensure their actions do not cause harm to the organization or individuals involved.
Ethical hacking is a vital component of modern cybersecurity strategies. In a world where cyber threats are becoming more sophisticated and widespread, ethical hackers play an essential role in helping organizations protect their data, secure their systems, and stay ahead of malicious attackers. By simulating attacks and finding vulnerabilities, ethical hackers contribute to a safer and more secure digital environment for everyone.
Whether you’re an individual looking to protect your personal data or an organization aiming to safeguard your systems, understanding and leveraging ethical hacking can make a significant difference. Ethical hackers are not criminals; they are the unsung heroes working to keep the digital world safe.





























































