What is a Phishing Attack?
Learn how phishing attacks evolve using AI and social engineering, their dangers, protection strategies, and real-world case studies from 2015 to 2024.

Have you ever received an email that felt urgent or suspicious, perhaps claiming to be from your bank or a popular service like PayPal? It might have told you to verify your account information to avoid being locked out. If you’ve encountered something like this, you’ve likely faced a phishing attack—a form of cybercrime that preys on human trust and urgency.
Phishing isn’t just a minor annoyance; it’s one of the most dangerous and prevalent threats in our digital world.
How Does Phishing Work?
Phishing is essentially digital deception where cybercriminals manipulate victims into sharing sensitive information or downloading malware. It’s a tactic that blends social engineering with technical trickery, and here’s how it unfolds:
1. Crafting the Bait
Attackers start by creating a message, often an email or text, designed to look legitimate. These messages frequently appear to come from trusted sources, such as:
-
Banks: "Your account has been suspended. Log in to fix this."
-
E-commerce platforms: "There’s an issue with your recent order."
-
Popular services: Netflix or Amazon alerts, complete with logos and professional language.
Ethical hacking, often used to test and strengthen systems against such threats, reveals that the precision in mimicking official communication is key to a phishing scheme's success.
2. Setting the Trap
Phishers include a mechanism to engage their targets:
-
Links: Clicking directs victims to a counterfeit website almost identical to the original.
-
Attachments: Opening files installs malware, often designed to siphon off personal or financial data.
-
Call-to-Action: The message urges immediate action, using fear (e.g., “Your account will be locked”) or urgency (e.g., “Act now to avoid charges”).
Ethical hackers, who test these tactics to bolster organizational defenses, frequently simulate such scenarios to educate users about identifying these red flags.
3. Stealing Information
When victims interact with these malicious elements, their sensitive information—login credentials, credit card details, or personal identification—is captured. This data is:
-
Used for financial theft or identity fraud.
-
Sold on the dark web to other criminals.
By understanding phishing mechanisms through ethical hacking simulations, companies can implement stronger countermeasures, train employees, and reduce the chances of falling prey.
Phishing thrives because it manipulates trust, fear, and urgency. By combining ethical hacking strategies and vigilance, individuals and organizations can better safeguard themselves against these increasingly sophisticated schemes.
What Are the Dangers of Phishing Attacks?
Phishing attacks pose significant risks to individuals, businesses, and governments. Let me highlight the key dangers:
1. Financial Loss
The most immediate consequence is losing money. Once attackers gain access to your accounts, they can:
-
Drain bank balances.
-
Make unauthorized purchases.
-
Redirect payments meant for others.
2. Identity Theft
Phishing often targets personal data like Social Security numbers, addresses, and birthdates. With this information, attackers can:
-
Open credit accounts in your name.
-
Commit fraud that damages your credit score.
3. Malware Infections
Phishing emails often include malicious attachments. Opening these can install spyware, ransomware, or keyloggers on your device. This malware can:
-
Monitor your activities.
-
Encrypt your files, demanding a ransom for access.
4. Compromised Business Security
In organizations, phishing can lead to:
-
Leaks of sensitive company data.
-
Unauthorized access to systems and databases.
-
Financial losses and reputational damage.
5. Erosion of Trust
Beyond tangible losses, phishing erodes trust. If attackers impersonate a brand, customers may lose faith in that organization—even if it wasn’t at fault.
Phishing isn’t just a minor inconvenience; its repercussions can last years. Recognizing these risks underscores why we must stay vigilant.
How Do I Protect Against Phishing Attacks?
Prevention is the best defense. Over time, I’ve developed a checklist that helps me and others safeguard against phishing. Here’s what I recommend:
1. Recognize the Signs of Phishing
Be aware of red flags, such as:
-
Generic Greetings: Legitimate organizations usually address you by name, not “Dear Customer.”
-
Suspicious URLs: Hover over links to see the actual web address before clicking. Phishing links often include misspellings or odd domains (e.g., account-login-bank.com).
-
Urgent Language: Be wary of messages that push you to act immediately.
2. Use Multi-Factor Authentication (MFA)
MFA adds an extra layer of protection by requiring you to verify your identity through another method (e.g., a text message or app notification). Even if attackers obtain your credentials, MFA can block their access.
3. Keep Software Updated
Outdated software can have security vulnerabilities. Regular updates ensure your devices and apps are protected against the latest threats.
4. Verify Before Trusting
If you receive an email or text that seems suspicious:
-
Contact the organization directly using official contact information.
-
Avoid using the links or numbers provided in the message.
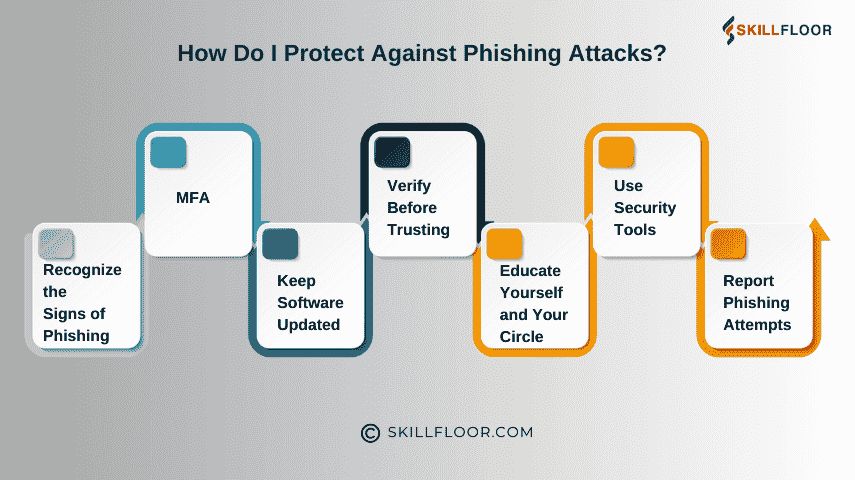
5. Educate Yourself and Your Circle
Phishing thrives on ignorance. By educating yourself, colleagues, and family members, you reduce the likelihood of falling victim.
6. Use Security Tools
-
Install antivirus software and keep it updated.
-
Use a spam filter to block suspicious emails.
-
Consider enabling browser tools that warn you about unsafe websites.
7. Report Phishing Attempts
If you encounter a phishing email, report it. Most email services have options to mark messages as phishing. Reporting helps organizations track and shut down scams.
How Do I Protect My Organization Against Phishing Attacks?
Businesses face a higher risk of phishing attacks because of the valuable data and funds they handle. Here’s how organizations can stay protected:
1. Conduct Employee Training
Employees are often the first line of defense. Regular training sessions on recognizing and responding to phishing threats can prevent breaches.
2. Implement Robust Email Security
Email filtering solutions can block many phishing attempts before they reach employees. Look for solutions that analyze links, attachments, and sender information.
3. Enforce Cybersecurity Policies
Establish rules such as:
-
No sharing of sensitive information over email.
-
Mandatory password policies and MFA usage.
4. Monitor and Respond Quickly
Organizations should have a plan for detecting and mitigating phishing incidents. Rapid response can minimize damage.
5. Use Endpoint Protection
Advanced cybersecurity tools can detect suspicious activities on devices, providing another layer of security.
Phishing attacks can cripple organizations if they’re not adequately prepared. A proactive approach can significantly reduce the risk.
Why Staying Vigilant is Crucial
Phishing attacks are evolving rapidly. Cybercriminals are becoming more sophisticated, leveraging advancements in artificial intelligence and social engineering to craft more convincing schemes that bypass even advanced cybersecurity defenses. What makes phishing so dangerous is that it exploits the most unpredictable element in cybersecurity—us, the users.
It’s all too easy to click on a malicious link in haste or open an attachment without a second thought. These moments of human error are precisely what attackers rely on to infiltrate systems and cause damage. This is why awareness, caution, and robust cybersecurity measures are essential to staying ahead of these threats.

Steps to Take After Falling Victim to a Phishing Attack
1. Disconnect Immediately
If you’ve clicked a suspicious link or opened a malicious attachment, disconnect your device from the internet to prevent further access to your system or network.
2. Change Your Passwords
-
Update passwords for any accounts that may have been compromised.
-
Use strong, unique passwords, and enable multi-factor authentication (MFA) wherever possible.
-
If you reuse passwords across sites (which is not recommended), update those as well.
3. Notify Relevant Parties
-
Bank or Financial Institution: If financial data was shared, inform your bank or credit card company immediately. They can monitor your accounts for fraudulent activity and potentially block transactions.
-
Employer or IT Department: If this happened on a work device or involves company accounts, notify your IT department right away.
-
Friends and Contacts: If your email or social media was compromised, warn your contacts to be cautious of any suspicious messages from your account.
4. Scan Your Device for Malware
Run a full system scan using antivirus or antimalware software. This will help detect and remove any malicious programs that may have been installed.
5. Monitor Your Accounts
Keep a close eye on your financial accounts and other sensitive accounts for unauthorized activity. If necessary, freeze your credit to prevent new accounts from being opened in your name.
6. Report the Incident
-
Report phishing emails to your email provider (e.g., by using the “Report phishing” option).
-
File a complaint with local authorities or cybercrime units in your country. In the U.S., you can report phishing to the Federal Trade Commission (FTC) or FBI’s IC3.
7. Educate Yourself for the Future
Reflect on how the phishing attempt succeeded and learn from the experience. Use it as an opportunity to better recognize and avoid similar attacks in the future.
Dealing with Emotional Impact
Falling for a phishing attack can be embarrassing or stressful, but it’s important to remember that it happens to people every day—even tech-savvy individuals. Take a deep breath and focus on resolving the situation rather than dwelling on it.
By taking quick and decisive action, most of the damage from a phishing attack can be mitigated or entirely prevented. If you’ve faced this issue, stay proactive and vigilant moving forward.
Defend Yourself and Others
Phishing is a serious threat, but it’s not unbeatable. By understanding how phishing works, recognizing its dangers, and following the protective steps outlined above, we can significantly reduce the risks.
Think of it this way: every time you pause before clicking a link or educate someone about phishing, you’re building a stronger defense against these attacks.
Let’s make the internet a safer place—together. What’s your experience with phishing? Have you ever spotted or fallen for an attack?
Major Phishing Cases and Their Lessons (2015–2024)
-
Google and Facebook Scam (2013–2015): A scammer posed as a vendor and tricked both tech giants into wiring over $100 million using fake invoices. This highlights the need for vendor verification and multi-level authorization.
-
DNC Breach (2016): Spear-phishing emails disguised as Google alerts targeted political figures, leading to leaked sensitive information during the U.S. elections. It showcased the geopolitical risks of phishing.
-
Google Docs Worm (2017): A phishing campaign mimicking Google Docs spread rapidly, granting attackers access to users' contacts and information. It emphasized securing third-party integrations.
-
Twitter Bitcoin Scam (2020): Cybercriminals hijacked high-profile Twitter accounts to promote a fake Bitcoin scheme, exploiting trust and revealing gaps in internal security protocols.
-
COVID-19 Exploits (2020 –2021): Phishers used pandemic-related fears, impersonating health organizations to steal personal data. The crisis underscored the value of employee awareness.
-
Cloudflare Attempt (2022): SMS-based phishing targeted Cloudflare employees, but strong multi-factor authentication prevented breaches, demonstrating the power of layered security.
-
MOVEit Data Breach (2023): A zero-day exploit led to a major breach, with subsequent phishing targeting organizations. It highlighted the role of opportunistic phishing post-breach.
-
AI-Driven Phishing (2024): Attackers used generative AI to create highly convincing phishing emails, bypassing traditional defences. This underscores the rising sophistication of phishing tactics.
Case study:- AI-Driven Phishing (2024)
In 2024, the advent of generative AI technologies like OpenAI’s GPT escalated phishing attacks to unprecedented levels. These attacks leveraged AI to craft convincing phishing emails and messages that were nearly indistinguishable from legitimate communications. This shift marked a significant evolution in cybercrime, making phishing campaigns highly effective and scalable.
How the Attack Worked:
Cybercriminals used generative AI to:
-
Create Hyper-Realistic Content: AI-generated messages mimicked legitimate corporate communication, including precise tone and branding.
-
Personalize Attacks: By analyzing data from social media or breaches, emails were tailored to individual targets, increasing credibility.
-
Automate Campaigns: Generative AI allowed attackers to launch large-scale phishing campaigns with slight variations in content to bypass spam filters.
-
Integrate Deepfake Media: While still emerging, there were instances of AI-generated voice and video used to impersonate high-ranking officials, making scams more believable.
Real-World Impact:
One high-profile case involved a major financial institution falling prey to an AI-driven phishing campaign. Fraudulent emails designed with generative AI mimicked the institution's internal communication style, leading to the compromise of several executive accounts. The attackers managed to infiltrate sensitive systems, exposing private data and causing reputational damage.
Detection and Response:
Despite the attackers’ sophisticated methods, a combination of multi-factor authentication (MFA) and anomaly detection tools thwarted the broader exploitation of the stolen credentials. This incident highlighted the critical importance of advanced cybersecurity practices, including:
-
Employee training to recognize AI-enhanced phishing.
-
Use of AI-powered tools to detect and block phishing attempts.
-
Implementation of a zero-trust security model.
Lessons Learned:
The rise of AI-driven phishing has demonstrated that traditional detection methods are no longer sufficient. Organizations must adopt a proactive approach to counter these threats, investing in both technology and awareness to stay ahead of evolving tactics. Cybersecurity experts emphasize the ongoing need for collaboration between industries and governments to strengthen defenses against such advanced threats.
For more details on AI and phishing, check resources like SiliconANGLE and Callsign.






























































