Cyber Security Scope in India: Jobs and Careers
Cybersecurity is booming as threats rise. Don't miss opportunities in ethical hacking, cloud security, and more. Start securing India's digital future today!

Did you know that in just the first quarter of 2023, India was the target of about 18 % of cyberattacks? This surprising number shows how important cybersecurity has become in the current digital environment. Having worked as an ethical hacker for more than five years, I have direct experience with how governments and companies scramble to protect their networks. India is emerging as a major participant in the constantly expanding demand for certified hacking professionals. If you've ever been wondering about the scope of cyber security in India, let me lead you through the opportunities, difficulties, and career paths in this exciting field. We'll cover the various roles, skills required, and career paths that make cybersecurity in India a very fulfilling field in this blog.
India is going through a digital change, with programs such as Digital India, the growth of online services, and an increased reliance on technology in many industries. But there is also a significant increase in cyber threats as a result of this connection growth. Strong cybersecurity protection is more important now than ever because of ransomware attacks that target companies and phishing scams that target people. At this point, India's cyber security scope becomes important. Cybersecurity presents a bright future full of varied opportunities, creativity, and the ability to have a practical effect on anyone thinking about a career in technology.
What is Cybersecurity?
Cybersecurity involves protecting data, networks, and systems from online hazards. It is not just seen in large enterprises; it is also found in sectors like banking, healthcare, education, and even the government. Experts in this area focus on preventing data breaches, making sure rules are followed, and reducing the risks brought on by cyberattacks. Cybersecurity has emerged as a key component of digital infrastructure in India, as digital ecosystems are growing quickly.
The Growing Demand for Cybersecurity in India
By 2030, the digital economy in India is expected to grow to $1 trillion. This expansion has led to an exponential rise in the potential for cyber hazards. According to recent figures, there were more than 1.9 million cyberattacks in India in 2022 alone. Given that cybersecurity is one of the fastest-growing job areas in this country, this concerning number emphasizes the important need for skilled professionals in this field.
For more information about the digital economy in India, refer: https://www.thehindu.com/business/dpis-to-help-india-achieve-1-trillion-digital-economy-by-2030/article67871914.ece#
Important Factors Driving Demand:
-
Rising Cyberthreats: Ransomware and phishing assaults against Indian companies are on the rise. This necessitates the use of qualified experts who can reduce risks and safeguard private information.
-
Regulatory Frameworks: Laws like the Personal Data Protection Bill highlight the importance of cybersecurity and open up job opportunities in a variety of sectors.
-
Corporate Investments: Businesses are investing heavily in creating strong security teams, and many are hiring Indian experts to handle cybersecurity operations.
-
Global Outsourcing Hub: India is a global outsourcing hub, and many multinational corporations depend on Indian cybersecurity professionals to keep them safe.
-
Critical Infrastructure Protection: As sectors like energy, transportation, and healthcare become more digitally integrated, there is a growing need for experts to protect these vital systems.
Career Opportunities in Cybersecurity
If you look into the Cyber Security Scope in India, you'll find a wide range of employment opportunities that suit different interests and skill sets. Let's explore them:
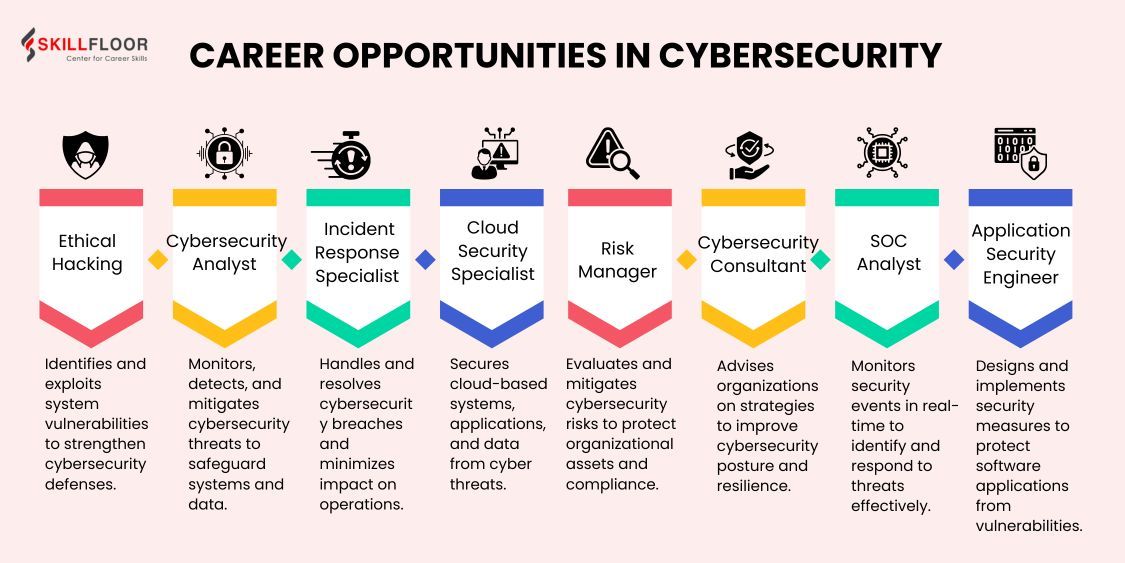
Ethical hackers, also called white-hat hackers, test systems to find and fix vulnerabilities. Organizations are focusing on security audits, which has made ethical hacking a desirable knowledge. Professionals in this position stay one step ahead of cybercriminals by using their knowledge to stop future attacks.
Skills Required:
-
Penetration testing tools (e.g., Metasploit, Burp Suite)
-
Knowledge of programming languages (Python, Java)
-
Problem-solving mindset
Certifications:
-
Offensive Security Certified Professional (OSCP)
2. Cybersecurity Analyst
These experts respond to security breaches and keep an eye on networks for unusual activity. Analysts in cybersecurity are often the first line of defence for safeguarding an organization's resources. To identify risks and ensure the security of important data, they employ advanced technologies.
Skills Required:
-
Intrusion detection systems (IDS)
-
Network security protocols
-
Threat intelligence
Certifications:
-
CompTIA Security+
-
GIAC Security Essentials (GSEC)
3. Incident Response Specialist
Incident response experts act in the event of a breach to prevent damage, recover lost information, and prevent attacks like this in the future. They play a crucial part in reducing the effects of cyber incidents and quickly getting things to normal.
Skills Required:
-
Crisis management
-
Malware analysis
-
Forensic investigation
Certifications:
-
Certified Incident Handler (GCIH)
-
Certified Information Systems Auditor (CISA)
4. Cloud Security Specialist
As cloud-based solutions become more widely used, cloud security experts concentrate on protecting cloud platforms and making sure data protection regulations are followed.
5. Risk Manager
Risk managers analyze and reduce the risks associated with cybersecurity. They are essential in making sure that company operations are not compromised.
Skills Required:
-
Risk assessment frameworks
-
Compliance knowledge
-
Strategic planning
Certifications:
-
Certified Risk Manager (CRM)
-
CISM (Certified Information Security Manager)
6. Cybersecurity Consultant
Consultants advise firms on best practices and technology while providing them with customized solutions.
Skills Required:
-
Industry knowledge
-
Excellent communication
-
Project management
Certifications:
-
CISSP (Certified Information Systems Security Professional)
-
ISO 27001 Lead Auditor
7. SOC Analyst (Security Operations Center Analyst)
SOC analysts are employed at Security Operations Centers, where they keep a close eye on risks and react quickly to events.
Skills Required:
-
SIEM tools (e.g., Splunk, QRadar)
-
Log analysis
-
Threat hunting
8. Application Security Engineer
Making sure software programs are free of vulnerabilities is the main goal of application security engineers.
Skills Required:
-
Secure coding practices
-
Vulnerability scanning tools
-
Software development lifecycle knowledge

Skills Required to Succeed in Cybersecurity
-
Technical Proficiency: It is important to know about operating systems, networking, and programming languages. Skills in Python, Java, and Linux are particularly valuable.
-
Problem-Solving Ability: Cybersecurity frequently calls for making quick choices under pressure. It is essential to be able to think analytically and solve difficult issues.
-
Adaptability: Because threats are ever-changing, experts must keep up with the newest techniques and trends.
-
Certifications: You can greatly improve your employment prospects by obtaining certifications such as CompTIA Security+, CISSP (Certified Information Systems Security Professional), or CEH (Certified Ethical Hacker).
-
Communication Skills: For many cybersecurity professions, the skills to explain technical concepts to stakeholders who are not technical is essential.
Educational Pathways to Enter Cybersecurity
It takes a combination of education, certifications, and practical experience to build a career in cybersecurity. Let's examine the possibilities:
1. Formal Education
-
Bachelor's Degree: It is strongly advised to have a degree in cybersecurity, information technology, or computer science.
-
Master's Degree: You can improve your chances by earning advanced degrees like an MBA in IT management or an M.Tech in cybersecurity.
2. Certifications
Credibility in cybersecurity is established by certifications. The following are a few of the most sought-after:
-
Certified Ethical Hacker (CEH)
-
CompTIA Security+
-
Certified Information Systems Security Professional (CISSP)
-
Certified Information Security Manager (CISM)
3. Online courses and boot camps
Excellent courses for beginners as well as professionals are available on platforms like Coursera, Skillfloor, Udemy, and EC-Council. Bootcamps offer immersive, hands-on, and practical learning experiences.
4. Hands-On Practice
You can gain practical experience by creating labs with programs like VirtualBox or VMware and practising on websites like Hack The Box or TryHackMe. To improve your skills, multiple experts recommend participating in Capture the Flag (CTF) competitions.
5. Specialization
Gaining expertise in innovative domains like cloud security, threat intelligence, or IoT security can lead to highly desirable jobs in particular sectors.
Top Industries Hiring Cybersecurity Professionals in India
1. Software and IT Companies
-
To protect their global operations, companies like Infosys, TCS, and Wipro are looking for cybersecurity experts. These businesses prioritize security because they handle enormous volumes of data.
2. Financial Services and Banking
-
To safeguard customer data and stop financial fraud, banks are giving cybersecurity top priority as online banking and digital transactions become more common. Organizations that are setting the standard for modern security measures include SBI, HDFC, and ICICI.
3. Healthcare
-
Sensitive patient data must be protected as healthcare becomes more digitalized. Healthcare tech companies and hospitals are making significant investments in cybersecurity solutions.
4. E-commerce
-
To protect their platforms and consumer transactions, businesses like Amazon and Flipkart make significant investments in cybersecurity. These platforms are becoming prime targets for hackers due to the rise in online purchasing.
5. Government Agencies
-
Strong cybersecurity protections are needed for government programs like Aadhaar and GST, which opens up chances for public sector companies. Professionals are being hired by agencies more frequently to protect the nation's digital assets.
Salary Expectations in Cybersecurity
There are great employment prospects in cybersecurity across a range of roles and experience levels, making it one of the most successful and in-demand fields today. The salary varies depending on skill, role complexity, industry, and geographic location. A detailed examination of cybersecurity pay in India is provided below, broken down by position and degree of experience.
Entry-Level Roles
Professionals working at the entry-level are mostly responsible for carrying out predetermined activities, helping to monitor systems, and responding to events while being supervised. Typical roles consist of:
-
Cybersecurity Analyst: ₹3-5 LPA
-
Penetration Tester (Junior): ₹4-6 LPA
-
Network Security Engineer (Junior): ₹3-6 LPA
Mid-Level Roles
Project management, security strategy implementation, and more advanced activities are frequently performed by mid-level experts. They are supposed to oversee categories, create safety protocols, and do thorough threat analysis. Common roles consist of:
-
Security Consultant: ₹7-12 LPA
-
Incident Response Specialist: ₹8-13 LPA
-
SOC (Security Operations Center) Manager: ₹10-15 LPA
-
Ethical Hacker: ₹7-12 LPA
Senior-Level Roles
Significant experience, leadership, and decision-making skills are necessary for senior positions. Professionals at this level work closely with the leadership team, manage sizable teams, and create security policies. Common roles consist of:
-
Chief Information Security Officer (CISO): ₹25-50 LPA
-
Security Architect: ₹20-35 LPA
-
Threat Intelligence Specialist: ₹20-30 LPA
|
Role |
Experience Level |
Average Annual Salary (₹ LPA) |
|
Cybersecurity Analyst |
Entry-Level |
3-5 |
|
Penetration Tester (Junior) |
Entry-Level |
4-6 |
|
Network Security Engineer (Junior) |
Entry-Level |
3-6 |
|
Security Consultant |
Mid-Level |
7-12 |
|
Incident Response Specialist |
Mid-Level |
8-13 |
|
SOC Manager |
Mid-Level |
10-15 |
|
Ethical Hacker |
Mid-Level |
7-12 |
|
Security Architect |
Senior-Level |
20-35 |
|
Threat Intelligence Specialist |
Senior-Level |
20-30 |
|
Chief Information Security Officer (CISO) |
Senior-Level |
25-50 |
Challenges in Cybersecurity Careers
While the cybersecurity scope in India is promising, professionals face a number of difficulties that require constant effort, adaptability, and resilience.
1. Rapidly Changing Technology
With the arrival of new technologies like AI and IoT, the cybersecurity landscape is changing at a rapid rate. To stay ahead of new hazards professionals need to constantly improve their skills, which takes a lot of time and work.
2. High-Stress Environment
Professionals in cybersecurity frequently handle high-pressure situations, such as responding to breaches or repelling attacks. These situations require making decisions quickly, working long hours, and, if not handled well, might result in burnout.
3. Skill Shortage
There is a huge skills gap since there is a far greater need for cybersecurity specialists than there is supply. Existing professionals are further burdened by this lack, which also limits the industry's capacity to fully address new risks.
4. Budget Constraints
Many businesses are unwilling to set up enough money for strong cybersecurity measures. This lack of investment may make it more difficult for experts to successfully apply innovative methods and equipment.
5. Compliance Challenges
Maintaining compliance with national and international cybersecurity regulations, like the GDPR or Indian IT rules, is a constant challenge. Professionals must stay up to date on changing laws and make sure their companies meet with them.
How to Start Your Cybersecurity Career in India
The following specific steps will help you get started on your journey:
-
Learn the Basics: Understand networking, operating systems, and coding basics.
-
Choose a Specialization: Identify the domain that interests you the most.
-
Get Certified: Pursue certifications to validate your skills.
-
Build a Portfolio: Showcase your projects and achievements.
-
Network: Join cybersecurity communities, attend events, and connect with professionals.
-
Intern or Freelance: Gain experience by interning or working on freelance cybersecurity projects.
-
Stay Updated: Follow cybersecurity news, trends, and tools to remain relevant in the field.
Tips for Aspiring Cybersecurity Professionals
-
Learn programming languages like Python and develop a strong understanding of networking at a young age. Excellent beginner courses are available on platforms such as Coursera, Skillfloor and Udemy.
-
To improve your skills, take part in cybersecurity boot camps, hackathons, or capture-the-flag (CTF) events. These real-world experiences are priceless.
-
Read blogs, listen to podcasts, and participate in forums like LinkedIn groups and Reddit's r/cybersecurity to stay current on the newest developments.
-
Create an effective professional network by attending cybersecurity conferences and using LinkedIn. Networking can lead to mentorship and job opportunities.
Future Trends in Cybersecurity
1. Artificial Intelligence (AI) in Security
AI is transforming cybersecurity by being used to detect threats more quickly and accurately. AI-powered tools can anticipate and stop threats before they happen.
2. Cloud Security
As more people turn to cloud-based solutions, protecting cloud infrastructure is becoming more and more important. Businesses are searching for experts who can protect multi-cloud settings.
3. Zero-Trust Architecture
This concept improves overall security by assuming that no user or device can be trusted. Organizations are implementing zero-trust frameworks to reduce insider risks.
4. Blockchain Security
Making sure blockchain technology is secure will lead to new opportunities in cybersecurity as it gets more widely used. Cryptocurrency and decentralized applications (DApps) need to be protected.
5. Quantum Computing
It is possible for quantum computing to crack traditional methods of encryption. Cybersecurity experts will be important in creating encryption methods that are resistant to quantum errors.
The Cyber Security Scope in India is growing at an unprecedented rate, providing not only jobs but meaningful opportunities that make a difference. The need for qualified people will only increase as India continues to embrace digitization. Cybersecurity is a field worth looking into whether you're a computer enthusiast, a problem solver, or someone searching for a steady and fulfilling career. Begin now, acquire the necessary abilities, and become one of the experts influencing India's digital future. You may play a key role in safeguarding India's digital environment if you have the correct attitude and commitment.
































































