Components of Cybersecurity
Protect your data & systems from cyber threats. Learn key cybersecurity components & best practices to stay secure in the digital world. Stay ahead of hackers!

Cybersecurity has become an essential part of my life, both personally and professionally. Every day, I cruise the digital world, aware of the circulating threats that could compromise sensitive information, disrupt operations, or even cause financial losses. Over time, I have come to appreciate the multiple layers of security that protect our data and systems.
Cybersecurity is the practice of protecting systems, networks, and data from cyber threats. The increasing reliance on digital technologies means that cyberattacks are more frequent and sophisticated than ever. Whether you are an individual, a business owner, or a cybersecurity professional like me, understanding the key components of cybersecurity is crucial to safeguarding critical assets.
Core Components of Cybersecurity
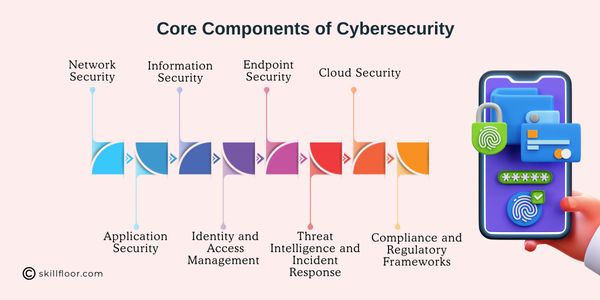
1. Network Security
I have always prioritized network security as it acts as the first line of defense against cyber threats. Network security ensures that unauthorized users do not gain access to private networks, preventing data breaches and cyberattacks. Some of the essential elements include:
-
Firewalls: Act as a barrier between a trusted internal network and untrusted external networks.
-
Intrusion Detection and Prevention Systems (IDS/IPS): Monitor network traffic for signs of malicious activity and take preventive action.
-
VPNs (Virtual Private Networks): Provide secure remote access to private networks, ensuring encrypted communication.
-
Network Segmentation: Isolates critical systems to reduce the attack surface.
2. Information Security
Protecting data is at the heart of cybersecurity. Information security focuses on maintaining the confidentiality, integrity, and availability (CIA) of data. Some of the measures I rely on include:
-
Data Encryption: Protects sensitive information by converting it into unreadable text, only accessible with the right decryption key.
-
Data Classification: Categorizing data based on sensitivity to implement proper access controls.
-
Data Loss Prevention (DLP): Prevents unauthorized users from transferring sensitive data outside the organization.
-
Backup and Disaster Recovery: Ensures data availability in case of cyber incidents.
3. Endpoint Security
Every device connected to a network represents a potential entry point for cyber threats. I always stress endpoint security to safeguard devices such as laptops, smartphones, and IoT gadgets. Key measures include:
-
Antivirus and Anti-malware: Detect and remove malicious software.
-
Endpoint Detection and Response (EDR): Monitors endpoint activities for suspicious behavior and responds to threats in real time.
-
Mobile Device Management (MDM): Controls and secures mobile devices used in the organization.
4. Cloud Security
With businesses and individuals shifting to cloud-based platforms, cloud security is more important than ever. I ensure that cloud environments remain secure through:
-
Cloud Access Security Brokers (CASB): Monitor cloud applications for unauthorized access.
-
Shared Responsibility Model: Ensures that both the cloud provider and users take responsibility for security.
-
Encryption: Protects data stored and transmitted through cloud services.
5. Application Security
I have seen firsthand how insecure applications can expose organizations to cyber threats. Application security involves protecting software from vulnerabilities through:
-
Secure Software Development Life Cycle (SDLC): Integrating security into the development process.
-
Web Application Firewalls (WAF): Protects web applications from cyber threats like SQL injections and cross-site scripting (XSS).
-
API Security: Ensures that APIs are protected from unauthorized access and abuse.
6. Identity and Access Management (IAM)
Identity and Access Management (IAM) controls who can access systems and data. I rely on IAM to ensure that the right people have access to the right resources. Key elements include:
-
Role-Based Access Control (RBAC): Restricts access based on job roles.
-
Multi-Factor Authentication (MFA): Requires multiple forms of verification.
-
Privileged Access Management (PAM): Manages access for high-level system users to prevent misuse.
7. Threat Intelligence and Incident Response
Cyber threats constantly evolve, so I integrate threat intelligence and incident response into my cybersecurity strategy. This involves:
-
Security Information and Event Management (SIEM): Collects and analyzes security data for real-time threat detection.
-
Threat Hunting: Proactively searching for potential security threats.
-
Incident Response Plans: Prepares organizations to handle cyber incidents effectively.
8. Compliance and Regulatory Frameworks
Adhering to compliance standards is non-negotiable. I make sure to follow industry-specific regulations, including:
-
General Data Protection Regulation (GDPR): Protects personal data in the EU.
-
Health Insurance Portability and Accountability Act (HIPAA): Secures healthcare data.
-
Payment Card Industry Data Security Standard (PCI-DSS): Ensures secure credit card transactions.
Advanced Cybersecurity Topics
Zero Trust Security Model
One of the latest security approaches I have embraced is the Zero Trust Security Model. It operates under the principle of "never trust, always verify."
-
Least Privilege Access: Users get only the access necessary for their tasks.
-
Micro-Segmentation: Limits movement within a network to contain threats.
Artificial Intelligence & Machine Learning in Cybersecurity
AI and ML have revolutionized cybersecurity by automating threat detection. I use AI-powered security tools to:
-
Identify anomalies in network traffic.
-
Predict and prevent cyber threats.
Ransomware & Malware Protection
Ransomware attacks are growing rapidly, and I take the following steps to mitigate them:
-
Regular data backups.
-
Deploying ransomware detection tools.
-
Employee awareness training to recognize suspicious links and attachments.
Social Engineering & Phishing Protection
Cybercriminals often exploit human psychology through phishing and social engineering attacks. I counter these threats with:
-
Email security filters.
-
Security awareness training.
-
Implementing strict verification protocols.
Blockchain & Cybersecurity
Blockchain technology has started playing a role in cybersecurity, particularly in securing transactions. It provides:
-
Decentralized identity management.
-
Cryptographic security.
-
Tamper-proof data integrity.
Best Practices for Strengthening Cybersecurity
To maintain strong cybersecurity, I always follow these best practices:
-
Regular security audits to identify vulnerabilities.
-
Keeping software and systems up to date.
-
Using strong password policies and Multi-Factor Authentication (MFA).
-
Conducting security awareness training for employees.
-
Monitoring network traffic and incident logs.
Regulatory and Compliance Aspects
Cybersecurity regulations and compliance frameworks set guidelines for organizations to protect data, manage security risks, and respond to incidents. These standards help businesses align with best practices and avoid legal consequences.
General Data Protection Regulation (GDPR)
GDPR is a European Union regulation that governs data protection and privacy. It applies to any organization that processes the personal data of EU citizens, regardless of where the company is based. Key principles include:
-
Data Minimization: Collect only necessary data.
-
Lawful Processing: Obtain user consent before collecting data.
-
Right to Access and Erasure: Users can request access to or deletion of their data.
-
Security Measures: Implement encryption and other safeguards to protect personal data.
Non-compliance can result in hefty fines, up to 4% of a company’s annual global revenue.
ISO 27001 Security Standards
ISO 27001 is an international standard for managing information security. It provides a systematic approach to securing sensitive information, covering:
-
Risk Assessment and Management
-
Access Control Policies
-
Security Awareness Training
-
Incident Response Planning
Organizations certified under ISO 27001 demonstrate commitment to cybersecurity, which can improve trust with customers and partners.
National Institute of Standards and Technology (NIST) Framework
The NIST Cybersecurity Framework is widely used in the U.S. for managing cybersecurity risks. It consists of five core functions:
-
Identify: Understand assets, risks, and vulnerabilities.
-
Protect: Implement safeguards like encryption and firewalls.
-
Detect: Monitor for security breaches.
-
Respond: Develop an incident response plan.
-
Recover: Ensure business continuity after an attack.
Many government agencies and businesses follow the NIST framework for improving cybersecurity posture.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is a security standard for businesses handling credit card transactions. It aims to prevent fraud and data breaches by enforcing:
-
Encryption of Cardholder Data
-
Strict Access Controls
-
Regular Security Testing and Monitoring
-
Implementation of Firewalls and Anti-Malware Software
Businesses that fail to comply risk fines, loss of processing rights, and reputational damage.
HIPAA and Cybersecurity in Healthcare
The Health Insurance Portability and Accountability Act (HIPAA) establishes security rules for protecting patient data. Healthcare organizations must:
-
Secure Electronic Protected Health Information (ePHI)
-
Control Access to Medical Records
-
Ensure Data Integrity and Backup
-
Report Data Breaches Promptly
Cyberattacks targeting hospitals can disrupt operations and compromise patient safety, making HIPAA compliance essential.
Emerging Cybersecurity Threats
Cyber threats evolve with technology, and attackers continue to exploit new vulnerabilities.
Ransomware and Malware Attacks
Ransomware is malicious software that encrypts data and demands payment for its release. Recent trends include:
-
Double Extortion: Attackers threaten to leak stolen data if ransom is not paid.
-
Ransomware-as-a-Service (RaaS): Cybercriminals sell ransomware tools to others.
-
Targeted Attacks on Critical Infrastructure: Healthcare, energy, and financial sectors are frequent targets.
Preventive measures include regular backups, employee training, and endpoint protection.
Phishing and Social Engineering Attacks
Phishing involves deceptive emails or messages that trick users into revealing sensitive information. Common tactics include:
-
Spear Phishing: Personalized attacks targeting specific individuals.
-
Business Email Compromise (BEC): Fraudsters impersonate executives to request fund transfers.
-
Voice Phishing (Vishing) and SMS Phishing (Smishing): Scammers use phone calls or text messages to deceive victims.
Multi-factor authentication (MFA) and security awareness training help mitigate these attacks.
Supply Chain Attacks
Cybercriminals target third-party vendors to gain access to larger networks.
-
Software Supply Chain Attacks: Malicious code is inserted into legitimate software updates (e.g., SolarWinds attack).
-
Hardware-Based Attacks: Compromised devices contain pre-installed malware.
Businesses must vet suppliers, monitor third-party access, and enforce strict security policies.
Deepfake and AI-Powered Cyber Threats
Deepfakes use AI to create realistic fake videos and voice recordings, leading to:
-
Political Disinformation: Fake speeches and news reports.
-
Corporate Fraud: Impersonating executives to authorize fraudulent transactions.
-
Cyber Espionage: AI-generated content used for blackmail or manipulation.
Detection tools and verification protocols are essential to counter deepfake threats.
Cybersecurity in Different Industries
Each industry has unique cybersecurity challenges due to the nature of its data and threats.
Cybersecurity in Finance and Banking
Financial institutions are prime targets for cyberattacks due to the high value of financial data. Common threats include:
-
Account Takeover Fraud: Attackers steal login credentials to access bank accounts.
-
ATM and Payment System Hacking: Malware and skimmers steal credit card details.
-
Cryptocurrency Fraud: Hacking of exchanges and digital wallets.
Banks implement biometric authentication, real-time fraud detection, and AI-driven risk assessments to enhance security.
Cybersecurity in Healthcare
Hospitals and clinics store sensitive patient records, making them attractive to cybercriminals. Key risks include:
-
Ransomware Disrupting Medical Services
-
Medical Device Vulnerabilities (e.g., hacked pacemakers, insulin pumps)
-
Data Breaches Affecting Patient Privacy
Healthcare providers use encryption, network segmentation, and staff training to prevent attacks.
Cybersecurity in E-commerce
Online businesses face threats such as:
-
Credential Stuffing Attacks: Hackers use stolen passwords to access accounts.
-
Fake Reviews and Fraudulent Transactions
-
DDoS Attacks Disrupting Online Stores
Secure payment gateways, fraud detection systems, and customer authentication methods like MFA help protect e-commerce platforms.
Cybersecurity in Government and Critical Infrastructure
Government agencies and essential services (power grids, water systems, and telecommunications) face cyber threats from nation-state actors. Risks include:
-
Cyber Warfare and Espionage: State-sponsored hackers target sensitive government data.
-
Infrastructure Disruptions: Attacks on energy grids can cause blackouts.
-
Election Security Concerns: Hacking attempts on voting systems.
Governments invest in cyber resilience, intelligence-sharing, and zero-trust security models to counter these threats.
Cybersecurity is an ongoing process that requires vigilance and adaptation. As threats evolve, so must our defenses. By understanding and implementing these components of cybersecurity, we can protect ourselves, our businesses, and our data from cyber threats. I strongly believe that cybersecurity is not just an IT issue—it is a shared responsibility for everyone in the digital space.
Let’s stay safe, stay informed, and be proactive in securing our digital world.































































