7 Steps in Ethical Hacking
Stop cyber threats before they happen! Learn the 7 Steps of Ethical Hacking to protect your organization from breaches and safeguard sensitive data.

Have you ever wondered how ethical hackers identify vulnerabilities that could cause organizations to fail to work? I have almost 5 years of experience as a cybersecurity expert, and I frequently come across this curiosity. Knowing how to get beyond security measures is only one aspect of ethical hacking; another is using an organized strategy to identify, understand, and eliminate risks. One of my most memorable experiences was working for a mid-sized business that accidentally released private information. We identified and fixed the problems using the 7 Steps of Ethical Hacking, protecting them from a potentially harmful breach.
Did you know that by 2025, cybercrime is predicted to cost the world more than $10.5 trillion, according to Cybersecurity Ventures? This figure shows the increasing demand for preventative actions, which is where the 7 Steps of Ethical Hacking are useful. I'll take you through these procedures in this blog, integrating industry best practices with useful advice to protect your digital data.
What is Ethical Hacking?
Ethical hacking involves looking into systems, networks, and applications to find defects that malicious hackers could exploit. The goal is to boost security by identifying weaknesses before they become threats, not to cause harm. In contrast to black-hat hackers, ethical hackers follow the law, have the right authorization, and have specific goals.
Businesses use ethical hacking to:
-
Making cybersecurity frameworks stronger.
-
Verify compliance with the protection of data laws such as HIPAA and GDPR.
-
Protect private customer information.
-
Create proactive protection against online cyberattacks.
The logical methodology offered by the 7 Steps of Ethical Hacking ensures that no security detail is missed. Let's examine each step completely and talk about the importance it is to protecting your digital environment.
7 Steps of Ethical Hacking
The organized process that ethical hackers use to find vulnerabilities in a system and strengthen its security is known as the "7 Steps of Ethical Hacking." Reconnaissance, scanning, access acquiring, access maintenance, privilege escalation, covering tracks, and reporting are among the procedures. Every stage ensures a methodical approach to identifying and addressing possible security flaws while following ethical norms.
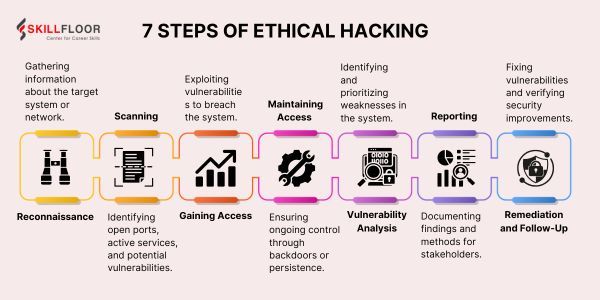
Step 1: Reconnaissance
The first step is reconnaissance, which involves collecting as much information as possible on a possible target. This information is used by ethical hackers to understand the infrastructure of the target and identify any potential vulnerabilities. There are two categories for this phase:
Passive Reconnaissance: Collecting publicly available data from websites, search engines, social media, and public records is known as passive reconnaissance.
Active Reconnaissance: Active reconnaissance is the process of actively probing a target using programs like Nmap or OpenVAS to look for accessible services or open ports.
For example, I used passive reconnaissance to find unencrypted employee email addresses during a cybersecurity assessment for a financial institution. These addresses were then used to help simulate phishing attacks. While active reconnaissance may involve mapping out the company's IP addresses, passive reconnaissance might entail looking through LinkedIn profiles to find personnel and their jobs.
The data acquired at this point serves as the basis for more thorough examination and focused testing in the next phases.
Step 2: Scanning
After laying the basis, ethical hackers proceed to the scanning phase, which is dedicated to identifying open ports, running services, and specific vulnerabilities in a system. Here, tools like Qualys, OpenVAS, and Nessus are frequently used.
Key types of scanning include:
- Port Scanning: Tools like Port Checker help them examine open ports to identify operational services and potential access points, a process known as port scanning.
-
Network Scanning: Mapping the linked devices, their settings, and any possible security threats is known as network scanning.
-
Vulnerability scanning: Pointing out known flaws in devices, software, or configurations that require quick fixes
For example, a vulnerability check performed during one project revealed that an organization's internal servers were running out-of-date software. These servers were easy targets for attack since they were running outdated software that the vendor no longer supported. Early remediation of these vulnerabilities stopped possible breaches from taking advantage of known weaknesses.
Step 3: Gaining Access
To gain access, one must take advantage of flaws that have been found to figure out how an attacker could get into a system. Although it is carried out inside the established limits of testing, this phase simulates real-world attacks. For penetration testing, programs like Metasploit, Hydra, or John the Ripper are frequently used.
For example, I identified weak user authentication procedures when evaluating an e-commerce platform. I showed how simple it was to get around their login mechanism using popular password dictionaries by simulating a brute-force attack. This highlighted the significance of putting multi-factor authentication (MFA) into place in addition to the dangers connected with using weak passwords.
In a different example, confidential customer data was accessed by taking advantage of incorrectly set-up privileges in a cloud environment. This emphasized the necessity of frequent audits and appropriate user role assignments.
It is important to document exploited vulnerabilities, steps taken, and mitigation recommendations during this phase.
Step 4: Maintaining Access
Once inside a system, ethical hackers model how a persistent attacker could work. This involves evaluating how long access can be maintained without detection. Commonly used methods include installing lightweight scripts for monitoring, establishing backdoors, and generating hidden user accounts.
I attempted to keep access using an incorrectly configured admin account during one interaction with a healthcare provider. By embedding a script in their database server, I demonstrated how attackers may exfiltrate sensitive patient information over time without being identified. Their intrusion detection systems (IDS) had serious flaws that were exposed by this.
Maintaining access helps businesses recognize possible hazards caused by prolonged access and points out the necessity of monitoring tools, timely log reviews, and anomaly detection procedures.
Step 5: Vulnerability Analysis
The main goal of vulnerability analysis is to evaluate the risks connected to vulnerabilities that are found. Ethical hackers help organizations in addressing key issues first by ranking vulnerabilities according to their potential impact. Raw data is converted into actionable intelligence in this step.
For example, a vulnerability analysis performed during an infrastructure assessment for a retail company found accessible APIs that might be used to retrieve data without authorization. By investigating these APIs, I found that they lacked sufficient authentication procedures, leaving client transaction data at risk. The company avoided serious financial and reputational harm by taking swift action to address these problems.
Patch implementation, software updates, frequent security audits, and the use of advanced safety measures like web application firewalls (WAFs) are frequently suggested.
Step 6: Reporting
A thorough report is necessary for an ethical hacker's work to be considered complete. This document acts as the organization's road plan for resolving concerns that have been identified. A well-organized report ought to contain:
Executive Summary: Outlining the main weaknesses and the overall security posture.
-
Technical Findings: Detailed descriptions of vulnerabilities, the identification process, and possible consequences.
-
Step-by-Step Exploitation: An explanation of the methods used to exploit vulnerabilities during testing.
-
Recommendations: Providing practical remediation alternatives, such as policy revisions and technical improvements.
In a single case, a thorough study for a software business placed an intense focus on protecting their database rights, user authentication procedures, and APIs. The startup greatly decreased its attack surface and increased the customer trust by implementing these suggestions.
Step 7: Remediation and Follow-Up
The last phase focuses on fixing the problems found during testing and making sure they stay fixed over time. Working together with IT teams, ethical hackers offer advice on patch implementation, configuration improvement, and policy enhancement.
For example, following my collaboration with a logistics company, I carried out a follow-up test to confirm that their communication systems were using stronger encryption techniques. We made sure there were no lingering vulnerabilities by keeping an eye on the network after remediation.
To help employees in identifying phishing attempts or social engineering techniques, ethical hackers may also provide training sessions. By empowering employees to act as the first line of defense, this type of training lowers the possibility that a human mistake may result in security breaches.
To know more about Ethical Hacking, visit: Ethical hacking training in Bangalore
Phone No: 7996969995
Why the 7 Steps of Ethical Hacking Matter
An organized method for proactively protecting digital resources is offered by the 7 Steps of Ethical Hacking. Here's why they are so important:
-
Proactive Defense: Finding weaknesses before attackers can take advantage of them is known as proactive defense.
-
Regulatory Compliance: Assists businesses in conforming to industry standards and data protection laws.
-
Increased Trust: Promotes client confidence by showcasing a dedication to security.
-
Savings: Reduces possible downtime and avoids expensive breaches.
Businesses can lower their risk of expensive breaches and keep their online presence safe by taking these precautions.
Essential Tools for Ethical Hacking
Ethical hackers use various tools to effectively carry out their tasks. These essential tools include:
-
Nmap: An effective tool for network reconnaissance and scanning. It assists ethical hackers in locating open network ports and services.
-
Metasploit: A popular tool for exploitation and penetration testing. It offers a framework for creating attack simulations in order to find weaknesses.
-
Wireshark: A real-time network traffic analysis tool. It aids in spotting possible breaches and questionable activity.
-
Burp Suite: Made for checking the security of web applications. It enables testing for vulnerabilities like as cross-site scripting and SQL injection.
-
Nessus: An all-inclusive network and system vulnerability scanner. It points up flaws and offers suggestions for fixing them.
The Role of Ethical Hacking in the Evolving Cybersecurity Field
The strategies used by malicious hackers change along with technology. Ethical hacking needs to change to meet new issues in cybersecurity field, such as:
-
IoT Security: New vulnerabilities are brought about by the quick expansion of connected devices. The goal of ethical hacking is to prevent exploitation of these gadgets and the networks that connect them.
-
AI-Powered Threats: To improve their attacks, cybercriminals are using AI. Ethical hackers have to understand these complex dangers and create defenses against them.
-
Cloud Infrastructure: Data security is becoming more and more important as companies go to the cloud. Finding and fixing flaws in cloud platforms is the main goal of ethical hackers.
-
Ransomware Mitigation: The frequency and complexity of ransomware assaults are rising. Ethical hackers create plans to stop, identify, and overcome these dangers.
Ethical hackers maintain their effectiveness in protecting systems from current risks by always learning new things and adjusting to new developments.
The technique of ethical hacking is essential in the current digital age. For companies of all sizes, the 7 Steps of Ethical Hacking provide a tried-and-true process for detecting and reducing threats, ensuring strong security. Recall that everyone shares responsibility for cybersecurity, and that taking preventative action now can avoid major problems ahead.
Have you ever thought about how these actions could advance your career or organization? Share thoughts, and let's talk about methods to improve digital security together.































































