Simple Guide to Cyber Security Technologies
Learn to use Cyber Security Technologies effectively to stay safe online, protecting your accounts, devices, and personal information by following best practices.

Cybersecurity is more crucial than ever because millions of people use phones, computers, and the internet every day for social interactions, business, and shopping. While you pay your bills, check your messages, and browse social media, every click and download has a hidden danger.
Cyber threats are everywhere, including viruses, hackers, and fake emails. They search for those who are careless. Problems might arise from even minor errors, such as clicking on a doubtful link. Good cybersecurity practices, even if they are simple, help shield your devices and personal data from these frequent online threats.
The secret is to use basic tools and understand the fundamentals. Strong passwords, firewalls, antivirus programs, and safe practices all have a significant impact. You can safeguard your data, accounts, and devices by following a few simple steps. You can stay safe every day if you pay a little attention.
What is Cybersecurity?
The practice of protecting your gadgets, accounts, and private data against internet attacks is known as cybersecurity. It entails easy actions like creating secure passwords, keeping software up to date, and exercising caution when clicking on links or emails. Effective cybersecurity helps shield your data from threats like viruses and hackers.
Everyone, not just large corporations, should be concerned about cybersecurity. It keeps you safe whether you're working from home, using social media, or shopping online. You may avoid issues and enjoy the internet without worrying about your personal information being taken by adopting a few simple habits and using the right software.
The Role of Cybersecurity in Safeguarding Our Digital Lives
-
Protects Personal Data: Cybersecurity helps prevent hackers from accessing your banking information and passwords. By safeguarding this information, identity theft and financial loss in routine digital actions are avoided.
-
Prevents Unauthorized Access: Strong security protocols prevent illegal access to your accounts or devices. This guarantees that your digital tools can only be used safely and confidently by you and those you trust.
-
Safeguards Online Transactions: Cybersecurity makes sure your money is safe when you shop or pay your bills online. This increases confidence in digital services and lowers the chance of fraud.
-
Maintains Device Safety: Computers, phones, and tablets are shielded from malware and viruses by cybersecurity. Frequent updates and basic safety measures prevent unplanned damage or slowdowns in equipment.
-
Protects Work and Privacy: Data is essential for everyday operations for people as well as companies. Understanding the significance of cyber security helps in preventing the theft or misuse of private or sensitive work data.
-
Supports Safe Online Habits: Smart practices, such as avoiding unsafe connections and creating secure passwords, are encouraged by good cybersecurity. Every day, these minor changes make the internet a safer and more pleasurable place.
Understanding the Core Principles of Cybersecurity
-
Confidentiality: Maintaining the privacy of sensitive and private information is what is meant by confidentiality. It should only be accessible by those who are allowed. By securing your papers, emails, and passwords, you can prevent hackers and unauthorized access to your data.
-
Integrity: Integrity guarantees that your data will remain precise and unaltered. Cybersecurity guards against malware, errors, and unauthorized individuals modifying or corrupting files and data.
-
Availability: Availability guarantees that your data and systems are always available when you need them. Maintaining continuous access while avoiding disruptions due to attacks or technical problems is made easier by being aware of the core principles of cyber security.
-
Authentication: Authentication verifies the users' identities. By using multi-factor authentication, account verification, and strong passwords, you can be sure that only authorized individuals may access your accounts and devices.
-
Non-Repudiation: Non-repudiation guarantees that online behavior may be confirmed and relied upon. Transactions or messages, for instance, can be verified as coming from a certain individual or source.
-
Accountability: Accountability keeps tabs on system modifications and actions. Cybersecurity maintains logs or records to hold users accountable for their behavior, preventing abuse and facilitating prompt problem identification.
Exploring the Different Types of Cyber Threats
-
Viruses and Malware: Malware and viruses are dangerous programs that can steal data or harm your device. They frequently infiltrate through downloads, dubious links, or compromised applications, slowing down devices or resulting in loss.
-
Phishing Attacks: Phishing attacks deceive you into providing personal information by using phony emails, messages, or websites. To prevent falling for scammers, always verify links and sender information before clicking.
-
Ransomware: Ransomware prevents you from accessing your files or system unless you pay. Strong security procedures and routine backups help prevent hackers from taking your data hostage.
-
Weak Passwords: Hackers may gain access to your accounts if you use passwords that are simple to figure out. Multi-factor authentication and strong, one-of-a-kind passwords keep accounts safer and stop unwanted access.
-
Spyware: Spyware stealthily keeps an eye on your activities and gathers information without your consent. Because it can monitor browsing, keystrokes, and private data, it's crucial to use antivirus software and stay away from unknown downloads.
-
Unsafe Wi-Fi Networks: Wi-Fi that is open to the public or unsecured can let hackers access your data. Using a VPN or encrypted connections helps keep private information safe when using the internet in public settings.
An Overview of Essential Cybersecurity Technologies
1. Firewalls
A firewall serves as a barrier to keep your devices safe from the internet. They shield your data and devices from internet threats, block malicious traffic, and stop illegal access.
-
Network Protection: Firewalls keep an eye on network traffic coming in and going out. They prevent unauthorized or dangerous access while permitting secure connections, protecting computers, phones, and other gadgets from online threats.
-
Custom Rules: You can restrict which apps or programs have access to the internet by setting rules in a firewall. This gives private information an additional degree of security.
-
Alerts and Reports: Reports or alerts can be generated by firewalls in response to anomalous activity. This enables you to respond swiftly to neutralize possible dangers before they become issues.
2. Antivirus Software
Antivirus software looks for dangerous apps like malware, spyware, and viruses on your devices. It ensures your devices function properly, eliminates risks, and protects your data. Understanding how viruses operate and how antivirus software defends against them is made easier by learning about ethical hacking.
-
Threat Detection: Malware, spyware, and viruses are detected and eliminated by antivirus software. They guard against malware or dangerous downloads that could affect your files, private data, or device performance.
-
Real-Time Protection: Many antivirus programs continuously check your gadget. They identify dangers as they arise, preventing malware before it may cause issues or jeopardize your personal data.
-
Automatic Updates: Regular upgrades are necessary for antivirus software to identify emerging threats. By keeping it updated, you can make sure your device is safe from the newest malware, viruses, and other internet threats.
3. Encryption
Only those with permission can read your data since encryption builds it up. It keeps your digital life safe by guarding against hackers and illegal access to private data, including banking information, emails, and texts.
-
Data Privacy: Encryption guarantees that your files will remain unreadable even if they are intercepted. Your personal information and work data are secure because only those who possess the correct key can access it.
-
Secure Communication: It is possible to encrypt emails, internet calls, and messages. By doing this, you can chat online discreetly and stop others from listening in or stealing your information.
-
Protection on Devices: Encrypting files on PCs, smartphones, and cloud storage is possible. This provides additional security in the event that your device is stolen, lost, or compromised.
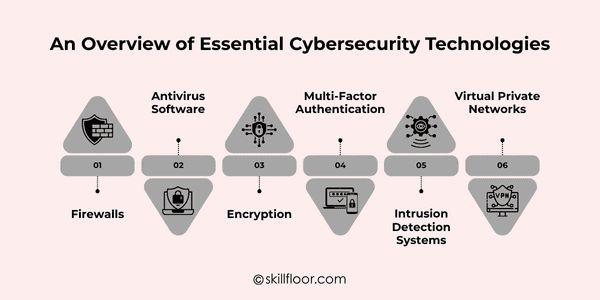
4. Multi-Factor Authentication (MFA)
Using multi-factor authentication gives your accounts an additional degree of security. It requires a second step, like a code or fingerprint, in addition to passwords. It is easier to see why MFA is crucial when one considers the impact of cybersecurity.
-
Extra Account Security: Hackers find it more difficult to access accounts with MFA. Your personal information is protected by the second verification step, even if someone knows your password.
-
Multiple Verification Methods: Codes, emails, SMS, and biometric scans can all be used for MFA. You can select the most practical and safe way for your accounts thanks to this flexibility.
-
Protection Across Devices: MFA is compatible with tablets, PCs, and phones. No matter where you log in, all of your accounts will remain safe if you enable it on several devices.
5. Intrusion Detection Systems
Intrusion detection systems keep an eye out for unusual activity on devices and networks. By warning you about possible dangers, they help stop attacks before they cause harm and protect your business and personal data.
-
Early Threat Alerts: IDS finds suspicious activities or odd behavior on your network. Early warnings let you take swift action, stopping malware or hackers from causing major issues.
-
Monitoring Network Traffic: IDS continuously examines data coming in and going out. It helps shield your devices from illegal access and cyberattacks by spotting suspicious connections and odd behaviors.
-
Support for Security Measures: IDS functions in combination with antivirus and firewall software. By providing you with knowledge about possible hazards, it improves overall protection by enabling you to take action before harm occurs.
6. Virtual Private Networks (VPNs)
A private, secure connection to the internet is made possible with VPNs. They help you surf safely and preserve your privacy online by hiding your location and protecting your data, particularly while using public Wi-Fi.
-
Secure Online Connections: By encrypting your internet connection, virtual private networks (VPNs) shield your data from hackers. This prevents unwanted access to your browsing history, passwords, and sensitive data.
-
Safe Public Wi-Fi Use: Wi-Fi in public places can be dangerous. By adding an extra layer of security, VPNs make it safer to shop online, check bank accounts, and check emails.
-
Privacy and Location Protection: VPNs conceal your location and IP address. By doing this, you safeguard your identity online and stop apps or websites from monitoring your browsing activity.
Emerging & Advanced Cybersecurity Technologies
-
Artificial Intelligence & Machine Learning in Security: AI and machine learning help in automatically identifying risks. By analyzing patterns, spotting odd behavior, and warning you of possible threats, they improve security and speed.
-
Zero Trust Security Models: Zero trust means never taking anyone or any gadget for granted. Because each login and access request are validated, the likelihood of cyberattacks or illegal access is decreased.
-
Cloud Security Solutions: Online files, applications, and services are safeguarded by cloud security. It guarantees secure access from any location, even when using numerous devices, and protects private information from hackers.
-
Blockchain for Security: Blockchain makes it difficult for data to be altered or tampered with. It makes transactions and records safer by ensuring honesty and trust.
-
Behavioral Analytics Tools: These technologies monitor user behavior to identify anomalous activity. Unexpected alterations in access or login habits aid in early threat detection and harm prevention.
-
Threat Intelligence Platforms: Platforms for threat intelligence gather information about new cyberthreats. They offer information and direction to help people and organizations get ready for and swiftly address emerging internet threats.
Best Practices for Implementing Cybersecurity Technologies
-
Keep Software Updated: Update your operating system, applications, and security software on a regular basis. Updates address security flaws and keep your devices safe from emerging malware, viruses, and other online dangers.
-
Use Strong, Unique Passwords: Make sure your passwords are lengthy, distinct, and challenging to figure out. To lower the chance of unwanted access, don't use the same password across several accounts.
-
Enable Multi-Factor Authentication (MFA): Use MFA to add an additional degree of security. The second verification step protects accounts from hackers, even in the event that a password is stolen.
-
Back Up Important Data: Make regular backups of your files to the cloud or an external drive. In the event that your device is lost, stolen, or attacked, this guarantees that you may retrieve your data.
-
Educate Yourself and Others: Learn about typical internet dangers, such as malware and phishing. Instruct friends, relatives, or coworkers on safe behaviors to lower the possibility of mishaps or assaults.
-
Start Small and Build Gradually: Start by putting basic security measures in place, such as firewalls, antivirus, and MFA. For more robust, multi-layered security, progressively incorporate more sophisticated techniques like behavioral analytics or VPNs.
The Future of Cybersecurity
Future cybersecurity will prioritize more intelligent tools and strong safeguards for all users. Advanced encryption, artificial intelligence, and secure cloud solutions will all help protect data as online dangers increase. Maintaining awareness of emerging threats and forming basic security practices will continue to be crucial. Everybody has a role to play in keeping their online safety and digital lives safe.
Using the right cybersecurity technologies and understanding the fundamentals can make staying safe online easier than it seems. You can protect your personal data from common attacks by utilizing multi-factor authentication, creating strong passwords, keeping your devices up to date, and following safe practices. While advanced technologies such as AI monitoring, cloud security, and threat intelligence can help you stay ahead of threats, essential tools like firewalls, antivirus software, VPNs, and encryption offer additional protection. By understanding the risks and taking small actions each day, you can create a significant impact on your online security. With a little thought and care, anyone can use the internet with confidence, safeguard their digital lives, and prevent issues before they arise.






























































